Zepto virus ransomware: how to decrypt .zepto extension files
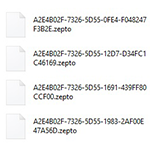
Learn a viable workaround to recover .zepto files ransomed by a new variant of the Locky crypto virus, which is currently on the rise after a lengthy halt. Discovering that most files on a computer suddenly got a .zepto extension is a frustrating scenario. Not only does this change denote an odd file display tweak, … Read more