Table of Contents
As ransom viruses are continually evolving, threats like the Locky virus end up in the spotlight because they feature enhanced extortion mechanisms.
When the .locky file extension virus emerged it instantly got a ‘special’ treatment on researcher’s end due to several unique characteristics. First off, as opposed to other ransomware, this breed is capable of encoding data stored inside network shares that aren’t mapped in the infected system’s hierarchy. This property makes the pest particularly hazardous for enterprise networks as it can rapidly propagate and freeze all corporate documents. Secondly, it’s using a mixture of Microsoft Office vulnerabilities and social engineering to run the initial instance of its malicious process. These non-standard traits set aside, Locky is a lot like the majority of crypto Trojans. Its trespass on a Windows computer is followed by a scan of the local hard drive sections and the external data repositories that the machine may be connected to.
Locky ransomware targets files with popular extensions and omits the ones that ensure stability of the operating system. As soon as the list of matching text documents, images, movies, spreadsheets, databases and presentations has been prepped, it’s time for the encryption routine proper. The virus leverages AES cipher for this purpose. Along with the encryption job, this infection also badly changes the filenames. Not only does it concatenate the .locky extension to all frozen objects, but it also replaces the original names with long strings of random digits and characters.
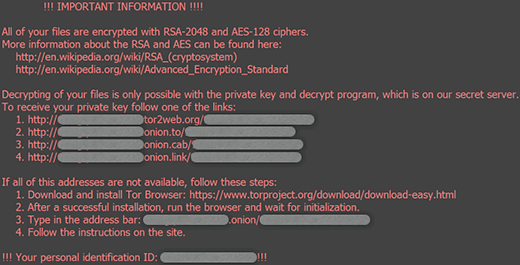
This being done, every folder with encoded data and the desktop get a new resident – the _Locky_recover_instructions.txt file. It holds the recovery steps that presuppose payment of 0.5 BTC, or around $200. The same directions are provided in the _Locky_recover_instructions.bmp document set as the new desktop wallpaper.
In a nutshell, to restore files the victim must visit a TOR page through one of the links listed in the ransom instructions. Then, they are required to provide their unique personal identification code on the .onion gateway titled Locky Decrypter Page, submit the money and download the decoder. Unlike some of its counterparts, the .locky virus doesn’t allow users to restore one or a few files for free.
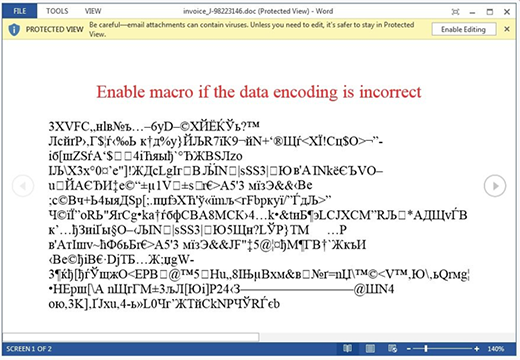
Now, a few words about the contamination technique. It’s not exploit-based, therefore users have a pretty good chance to avoid the problems if they are cautious enough. Locky is executed on computers through bogus invoices that go with phishing email messages. The attached Word document, when opened, looks completely illegible and recommends the person to enable macros in order to make it readable. This is how an exploit is deployed on the machine. Obviously, it won’t happen if the user ignores the macros activation prompt.
It’s impossible to circumvent the encryption by Locky ransom Trojan for the time being. However, paying the ransom isn’t an agreeable thing either. Before doing so, please try a couple of tips and tricks to learn how to get data back without messing with AES algorithm.
Automatic removal of .locky virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download .locky removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get .locky automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover .locky files ciphered by the ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of .locky virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.




Dear Sir,
Please advise how I can remove locky virus from xls files.
Thanks
GAUTAM
Gautam,
Try the steps above and see if it helps.
my 10 years data has been vanished due to locky virus
Hi , I was infected by locky and followed your instructions with shadow explorer and the results were positive.Unfortunately when the infection was taken place I had my external backup disc connected and the infection also spread there.The shadow explorer can’t read the external disc.Can you help?
Costas,
Glad we helped restore some of the .locky files. Regarding the backup disk, consider running the data recovery tool provided in this guide.
Hi, thank you for the insightful explanation. I did not have ‘restore points’ implemented so I have no ‘previous versions’. Is there any way to decrypt/restore the corrupted files ?