Table of Contents
Ransomware being today’s dominating cyber threat, infections like TeslaCrypt 3.0 are defiantly extorting money from users and organizations on a large scale.
A trojanized computer is a major headache for the victim. The severity of contamination, though, tends to vary based on the type of malicious code that’s encountered. While some trojans run silently in the background and monitor the user’s activity, pests like ransomware cause a lot more appreciable damage. They make one’s files inaccessible and extort a recovery fee afterwards. TeslaCrypt 3.0 is currently at the very top of the malware ‘food chain’. It is one of the prevalent ransom infections targeting both individuals and enterprises. The HDD volumes, USB drives and mapped network disks get scanned for hundreds of popular file extensions, with the spotted matches being encrypted with AES. This algorithm isn’t the most complex one in the cryptographic domain, but it’s still nearly impossible to crack.
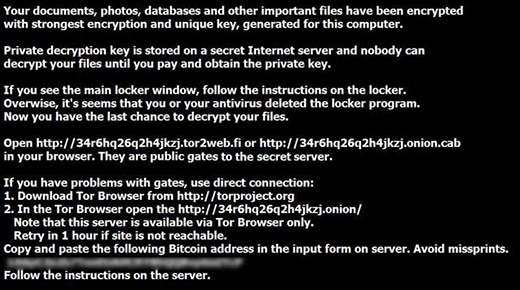
TeslaCrypt 3.0 exploits human vulnerabilities rather than loopholes in software to infect computers. The entry point most frequently used is spam webmail. In particular, people receive messages pretending to be someone’s CV, a bill, prize win congratulations, a traffic violation notice or delivery tracking details. The email itself is harmless, unlike the attachment that goes with it. It’s typically a ZIP archive that self-extracts once double-clicked, which means that the ransom code will be executed instantly and unnoticeably. Another vector of infecting workstations is the use of exploit kits such as Neutrino, but it’s quite rare at this point. So it’s strongly recommended to think twice before opening documents attached to messages from unknown senders or even suspicious ones from your contacts whose mail accounts may have been hacked.
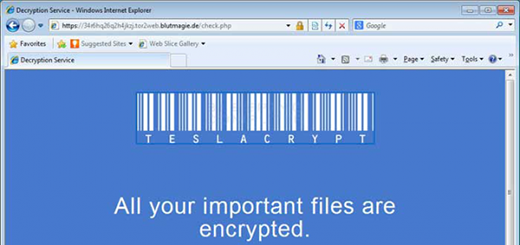
The personal file encryption process is followed by a ransom screen appearing out of the blue. TeslaCrypt 3.0 uses several components to communicate with the infected person. First off, it’s the application GUI proper, which says “All your important files are encrypted” and contains built-in buttons to show files, decrypt them or click to copy the Bitcoin address to clipboard. The virus also creates ransom note files on the desktop: Howto_Restore_FILES.HTM, Howto_Restore_FILES.TXT and Howto_Restore_FILES.BMP. These hold basically the same details as the main console. Furthermore, some variants of the trojan modify the desktop wallpaper to constantly remind the user of itself.
Not only do the affected files get encrypted, but they are also changed in terms of the extensions. Every object gets .micro, .ttt or .xxx added to its original name. In order to make the information available again, the victim is told to pay 1.5 BTC or more, which is usually an equivalent of $500. So far, there is no foolproof way to restore files without submitting this ransom, although there can be no certainty that even paying up is going to get the data back. What’s worthwhile, however, is a number of alternative methods covered below. Please be advised the efficiency of remediation depends on several factors, such as whether or not System Restore was enabled on the PC at the time of the attack, as well as the specific build of the trojan.
Automatic removal of TeslaCrypt 3.0 virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download TeslaCrypt 3.0 removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get TeslaCrypt 3.0 automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Decrypt .micro files locked by the ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of TeslaCrypt 3.0 virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.



