Table of Contents
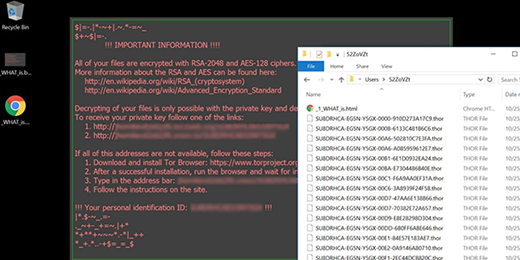
When a ransomware variant called Locky infects a computer, it displays a warning message saying that all files are encrypted with RSA-2048 and AES-128 ciphers.
There are ransomware attack occurrences where online crooks deliberately exaggerate the strength of data encryption in order to make the predicament look scarier than it actually is. Inflating the entropy of the decryption key is a prime example of this manipulation. What about the Locky ransomware case? This strain replaces a victim’s desktop wallpaper with the _WHAT_is.bmp image that says,
“All of your files are encrypted with RSA-2048 and AES-128 ciphers”
Is this alert true? Unfortunately yes. The Locky cyber-baddie first applies the symmetric AES (Advanced Encryption Standard) cryptosystem, which generates a secret key applicable for encoding and decoding alike. To further protect this AES key from being retrieved by a victim, the ransomware then encrypts it using asymmetric RSA-2048 algorithm. This one is yet tougher to crack.
It’s quite easy to avoid the Locky ransomware, because its intrusion usually requires certain direct action on a user’s end. More specifically, the contamination won’t take place unless a potential prey opens a booby-trapped email attachment. This infection paradigm involves a botnet-powered spam campaign and malicious scripts delivered with these phishing emails. The payload proper arrives with a ZIP file disguised as a receipt, curriculum vitae, bill, invoice, order information, cancellation request, or job offer. When an unsuspecting recipient unpacks this archive, they will see a random-named JS or VBS file. Once double-clicked, this script triggers the perpetrating code execution routine. Long story short, all it takes to stay away from this crypto infection is to click responsibly, especially when it comes to email attachments.
Before Locky gets down to encrypting one’s data, it determines what exactly is subject to this encryption. To do it, the ransomware silently scans the hard disk, removable drives and network shares, comparing every file it encounters against a build-in database of popular extensions. Having thus worked out what to scramble, the offending program makes the files inaccessible through the use of the aforementioned RSA-2048 and AES-128 cryptographic standards. Filenames get replaced with 32 characters that are followed by the .zepto, .odin, .thor, .osiris etc. extensions.
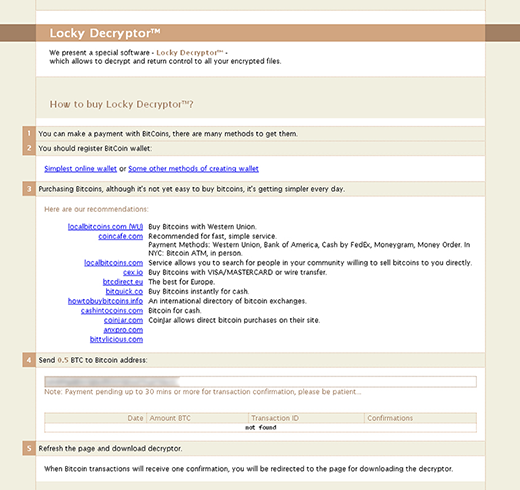
Ransom notes called _WHAT_is.html and _WHAT_is.bmp will appear on the desktop and inside affected folders. Their purpose is to notify the infected user what they must do to decrypt their personal data. The final destination in this extortion webwork is a Tor gateway titled the “Locky Decryptor page”. It provides the victim with down-to-earth details regarding the ransom size and the ways to pay it. The amount is typically 0.5 BTC, which equals 357 USD at this point. Every victim who is unwilling to pay this ransom – hopefully that’s the overwhelming majority – should follow some of the best practices of white hat file recovery.
Automatic removal of the RSA-2048 and AES-128 virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download RSA-2048 and AES-128 removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get RSA-2048 and AES-128 automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files encrypted with RSA-2048 and AES-128 ciphers
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of RSA-2048 and AES-128 virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.



