Table of Contents
Get viable methods to recover files encrypted by Fantom, a ransomware sample that displays a fake Windows update screen to conceal the data encryption process.
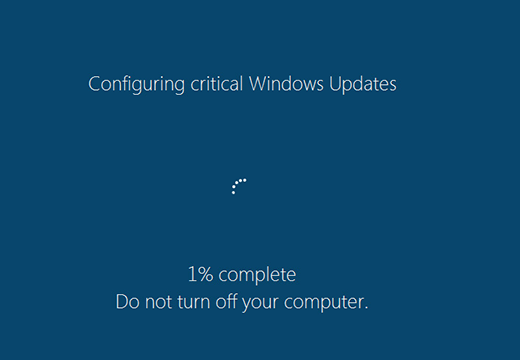
Operating system updates are occurrences that users take for granted as they are tasked with enhancing Windows stability and security. Cyber-threat actors, in their turn, have devised a way to take advantage of this inherent trust in order to arrive at their offending objectives. Having surfaced in late August, the strain of ransomware dubbed Fantom has had big success in contaminating computers on a large scale. The zest of this extortion campaign is all about masquerading the data encryption process as a critical OS update. As a result, the targeted people take their time and patiently wait for the routine to go all the way while their irreplaceable data is actually being scrambled with an unbreakable crypto algorithm.
According to extensive analysis of its code, the Fantom ransomware is based on EDA2, an open-source project originally intended as an educational initiative. This questionably benign contrivance by Turkish security enthusiast Utku Sen has already called forth serious security concerns, because ransomware distributors around the globe have been heavily harnessing it to craft real-world infections. The same applies to Fantom – it leverages the AES-128 cryptographic system to lock a victim’s personal files, concatenates the .fantom extension to each one, and then demands a ransom to restore the data. Flower.jpg.fantom is an example of what an arbitrary file will look like after being processed by the virus.
The fact that the Fantom executable pretends to be a critical Windows update and even bears some formal properties thereof is a problem, because security software running on the PC is less likely to identify it as malware. While the phony update progress is presented to the victim, the infection scours all data repositories for files with certain extensions that may indicate that they are important to the user. Fantom scans fixed drive volumes, removable drives such as memory sticks or other external hardware, and network shares. When the totality of personal entries have been found, the ransomware uses a previously generated 128-bit AES key to encode them. Unfortunately, this secret key is nowhere to be found on the machine itself – instead, it is stored on the cybercrooks’ C2 server.

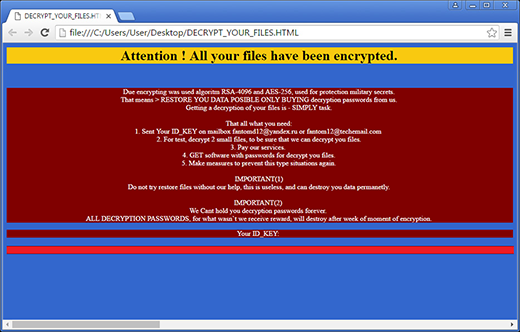
Then, the ransom Trojan enters the active user interaction phase. It creates a document named Decrypt_Your_Files.html inside every single folder with ciphered contents. This ransom note contains decryption instructions and provides the user’s unique ID key. According to the file, which is written in poor English, the victim needs to send their enclosed ID to [email protected] or [email protected]. The con artists will then respond with further steps regarding how much and in what way to pay the ransom. To prove that the decryption service actually works, the perpetrators offer free recovery of 2 small files.
To add insult to injury, Fantom ransomware also replaces the desktop wallpaper with a warning screen that says, “All files are encripted!!! [sic]” and provides the same email addresses as in Decrypt_Your_Files.html file. The numerous spelling and grammar errors, however, don’t make this crypto infection any less sophisticated. Security researchers have not managed to create a free decryptor for this sample, consequently victims have to either pay the ransom or try a couple of alternate methods to get their data back.
Automatic removal of .fantom virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download .fantom removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get .fantom automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover .fantom files ciphered by the ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of .fantom virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.



