Table of Contents
Being infected with GandCrab 5.2 ransomware is beyond frustration – it’s a serious quandary that entails a denial of access to data and loathsome extortion.
Most people who are more or less familiar with computer security have heard about ransomware. This despicable phenomenon has been a newsmaker for years. However, very few know the real impact of such an attack unless they have been hit at least once. One’s precious digital memories in the photos and videos, as well as valuable work files and a ton of other personal information – all of these suddenly become inaccessible and no one can ensure recovery whatsoever. No wonder the common reaction is a mix of panic, despair, and outright anger.
This is exactly what the GandCrab 5.2 onslaught looks like. This variant of today’s most heavily discussed ransomware strain splashed onto the landscape a couple of days after a researchers-tailored free decryptor was out. Here’s the thing: the recovery tool cracks GandCrab mods up to v5.1, but it’s completely inefficient for decrypting the edition under scrutiny due to some urgent “fixes” made by the crooks. It’s the crypto implementation that underwent the most tangible change in the newest version.
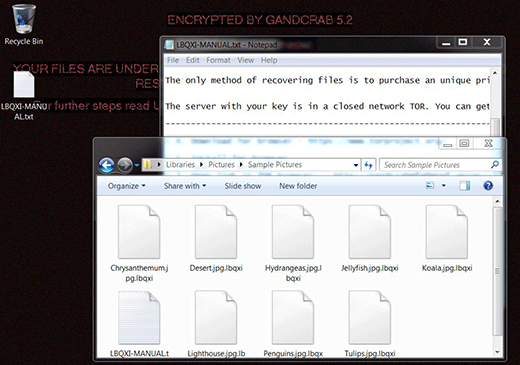
Most characteristics of GandCrab 5.2 bear a close resemblance to its precursors’ quirks or don’t differ at all. It still concatenates a random-looking extension to hostage files, the string being uniquely generated for every plagued computer. The length of this victim ID is a variable parameter and ranges from 5 to 10 characters. When an arbitrary file is encrypted it assumes a shape similar to this: Shark.png.iblkoqnt – notice the victim-specific extension following the original filename. Another essential element of the attack is the ransom note that’s created on the desktop and inside folders with the hijacked files. Its name consists of the above-mentioned file extension made uppercase, plus the word “DECRYPT” or “MANUAL” (e.g. IBLKOQNT-DECRYPT.txt). The different structures of this document’s name and the file extensions one can encounter in the wild can be explained by the fact that GandCrab 5.2 is distributed by multiple cybercriminal groups under an umbrella of the same RaaS (Ransomware as a Service).
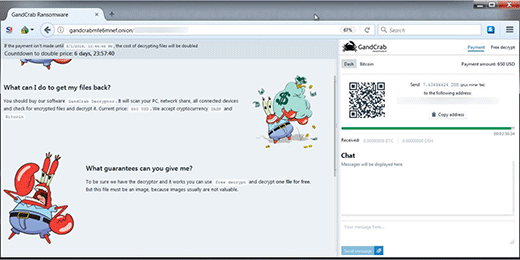
In addition to these indicators of compromise, the attack is accompanied by a replacement of the desktop wallpaper image. The infection sets a new one that says, “Encrypted by GandCrab 5.2. Dear [username], your files are under strong protection by our software. In order to restore you must buy decryptor. For further steps read [VICTIM ID]-DECRYPT.txt that is located in every encrypted folder”. Basically, this says it all. The user is instructed to visit their personal decryptor page via Tor browser. This resource indicates the precise size of the ransom, which can range from $600 to $1,200. There is a 7-day deadline to make the payment. After it expires, the ransom will double.
GandCrab 5.2 is mainly doing the rounds by dint of malicious spam. The target users receive malware-riddled Word documents disguised as an inquiry, invoice, job offer or another curiosity-driving file. When opened, the attached object prompts the recipient to enable macros otherwise they won’t see the content in it. This is a trap that launches scripts downloading the ransomware behind the scenes. This particular variant is also spreading over hacked remote desktop services and by means of exploit kits that harness unpatched software to drop the payload. At the end of the day, the consequences are equally harsh regardless of the propagation method. To sort them out, follow the recommendations below and be sure to take extra precautions to prevent such raids in the future.
Automatic removal of GandCrab 5.2 ransomware virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download GandCrab 5.2 removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get GandCrab 5.2 automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files ciphered by the GandCrab 5.2 ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of GandCrab 5.2 virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.



