Table of Contents
GandCrab 5.0.4 is one of the newest ransomware perils to watch out for, so you’d better be aware of its attack vectors, ensuing risks, and recovery tips.
No malicious computer code is as harmful as ransomware nowadays. Having fallen victim to one of these nasty entities, you can’t sort things out by running a powerful antimalware solution or even reinstalling the operating system. The reason is all about crypto – such infections encrypt data and hold it for ransom. The recently released GandCrab 5.0.4 strain is just like that. It represents a prolific lineage that emerged on the extortion arena at the beginning of 2018 and has since evolved significantly. This particular iteration is characterized by a number of unique attributes. It appends a random-looking extension to filenames after the cryptographic blow has been inflicted. An example is the modification of a file named Sample.xlsx into Sample.xlsx.mxvpbsnb. It’s not clear so far how exactly the pest comes up with these extensions, but they are unique per infection instance.
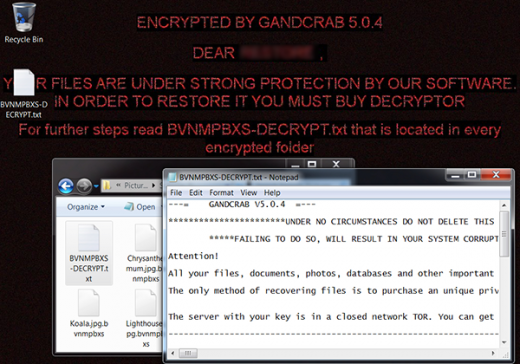
A ransomware onslaught would be incomplete without ransom notes. GandCrab 5.0.4 provides ones, too. These are multiple copies of a TXT document whose name consists of the string that matches the above-mentioned file extension, except that it’s in uppercase format, and the word DECRYPT. In the example we have provided, this how-to manual is going to be named MXVPBSNB-DECRYPT.txt. It lets the victim know that their “files, documents, photos, databases and other important files have been encrypted” and emphasizes that the only way of restoring the data is to purchase the unique private key stored on the crooks’ Tor (The Onion Router) based server. This is the fundamental issue with ransom Trojans – the recovery would be easy if the appropriate decryption key were at the user’s disposal, which isn’t the case here. So, the prey is then forwarded to a Tor page with the payment steps (see screenshot below).
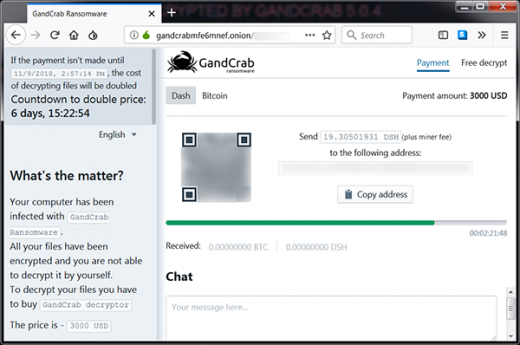
The payment page upsells what’s called the GandCrab decryptor for a specified amount of cryptocurrency. The ransom is payable in two ways: either with Bitcoin, or another digital currency called DASH. Its size is very variable. It can reach several thousands of dollars, with the lowest reported price being $800 worth of BTC or DSH. Unless paid during 7 days from attack time, the ransom will increase two times. To show that the money won’t be wasted and the decryptor does work, the criminals offer the victim to test it by uploading one hostage file and letting them reinstate it to its normal form. Interestingly, they point out that this item must be an image, saying that “images usually are not valuable”. Whatever.
By the way, one more prominent property of GandCrab 5.0.4 is that it drops an image named pidor.bmp onto the infected host and replaces the user’s desktop background with it. That’s one more way the ransomware intimidates the victim. The warning says, “Encrypted by GandCrab 5.0.4. Dear [username], your files are under strong protection by our software. In order to restore it you must buy decryptor. For further steps read [random]-DECRYPT.txt that is located in every encrypted folder”. No matter how spooky the attack may appear, those infected should abstain from paying the ransom. Instead, a few simple forensic tips may come in handy as far as file restoration is concerned. And last but not least, be careful with email attachments that look fishy – that’s the primary distribution method for GandCrab 5.0.4 and most other cryptoviruses.
Automatic removal of GandCrab 5.0.4 ransomware virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download GandCrab 5.0.4 removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get GandCrab 5.0.4 automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files ciphered by the GandCrab 5.0.4 ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of GandCrab 5.0.4 virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.