Table of Contents
Stay on top of the CTB Locker ransomware propagation vectors, learn what new features its latest version accommodates and how to restore encrypted files.
When it comes to moneymaking, cybercriminals have not contrived a more efficient instrument for this purpose than ransomware. Well, perhaps the only rivals are banking Trojans, but deploying those is a much riskier venture from the law enforcement perspective. The present-day online extortionists who create and distribute file encrypting programs like CTB Locker have become very good at thwarting attack attribution. Primarily, that’s because they use Tor (The Onion Router) as the main medium for data exchange between victims and C2 servers. Secondly, the ransoms are payable in Bitcoins only. Both of these systems ensure anonymity of transactions, which explains why cybercrooks behind the nastiest ransom Trojans have been on the loose for years.

CTB Locker, also referred to as Critroni, was one of the first strains that could be disseminated as Ransomware-as-a-Service (RaaS). What this means is different cyber gangs can buy its loader on some shady forums for 3000 USD, customize their build and spread it however they wish. The authors of the code proper get a share of ransoms submitted by victims afterward. It’s like an affiliate platform, only an illegal one.
Regardless of who exactly deposits CTB Locker on a PC, the symptoms are uniform. The payload drops the malicious executable into the Temp path, from which it will be launched every time Windows starts up. By the way, this is kind of a trick because most antiviruses are on the lookout for suspicious activity from entities located under Program Files and several other directories, not Temp. So it’s an AV evasion technique to some extent. Furthermore, the name of this executable tends to change with every new OS boot event.
When launched, the ransomware performs a hunt for valuable data, scanning all fixed drives, external physical ones and mapped network shares. When CTB Locker detects files that are most likely personal, such as .docx or .bmp items, it encrypts them using a cryptosystem called ‘elliptic curve cryptography’ (ECC). The files therefore cannot be opened or edited, plus the Trojan appends a new extension to each one. These used to be .ctbl or .ctb2 extensions, but recently the offending program started using random ones like .dmmkfrc.
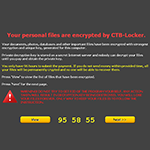
To let the victim know what happened to the data and what to do next, the ransomware changes the desktop background to ‘AllFilesAreLocked[user_ID].bmp image, which says “Your personal files are encrypted by CTB Locker”. This screen also counts down the time left from the original 96 hours, after which the ransom of 0.2 Bitcoins will double. It also creates similar ransom instructions in TXT and HTML format: DecryptAllFiles[user_ID].txt and [random].html, respectively. The newest edition of the virus allows users to recover 5 files for free. Is it possible to get the rest of the data back without paying up to the malefactors? If there is an offsite backup, yes. Otherwise, it depends. In any case, it won’t hurt to try the methods below and see if they can be of help.
Automatic removal of CTB Locker virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download CTB Locker removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get CTB Locker automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files ciphered by CTB Locker ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of CTB Locker virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.