Table of Contents
Being hit by the RSA-4096 ransom Trojan isn’t that much of a jeopardy if the user efficiently gets rid of the infection and follows several recovery steps.
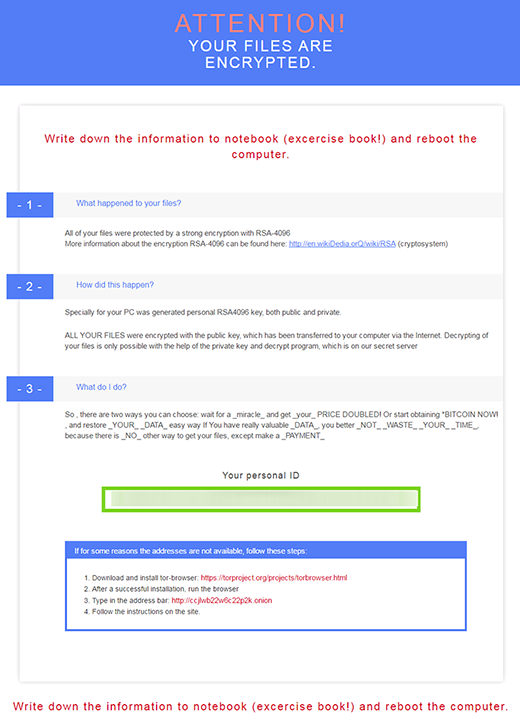
“Attention! Your files are encrypted.”
When confronted with a file encrypting ransomware sample, it may be difficult to tell the bluff from the truth. For example, a couple of widespread strains generate alerts about an alleged use of the RSA-4096 public-key cryptosystem to encipher their victims’ proprietary files, although this statement should not be taken for granted. These include TeslaCrypt and the more recent CryptXXX threats for the most part. Fortunately, there’s some good news regarding TeslaCrypt: the cybercrooks in charge of this campaign abandoned the malicious project in late May and released the master decryption key for all infected users to restore their frozen data without paying up. However, the above-mentioned CryptXXX appears to have inherited the nastiest characteristics of this now extinct virus.
Getting back to the subject matter of this post, the allusion to RSA-4096 algorithm is more of an intimidation trick rather than the genuine state of things. According to the analysis of CryptXXX code done by security professionals who looked into the issue, this ransomware is more likely to use a combination of AES-256 and RSA-2048 to encrypt files. This, of course, doesn’t mean that the remediation is any easier, because this mix is uncrackable and the perpetrators have implemented the crypto flawlessly.
And yet, the digital threat in question does not indicate its name anywhere in the ransom notes that it creates to instruct users regarding file decryption, therefore people tend to identify and look up their problem by the RSA4096 term. By the way, the software that the cybercrooks promote for decrypting the data is dubbed “Microsoft decryptor”. The ransom instruction documents are titled “README.html”, “README.txt”, and “README.bmp”. CryptXXX drops them into every path with encrypted data. They read “Attention! Your files are encrypted”.
This ransomware is promoted by means of an exploit kit known as Angler. For the attack to take place, the hackers need to make sure users are redirected to the exploit kit’s page. This happens in the event that the person visits a compromised website that has an obfuscated reroute script added to its code. Then, if there is an unpatched version of Java or Adobe Flash Player on the computer, the infection uses these vulnerabilities to directly inject the ransomware and execute it behind the scenes.
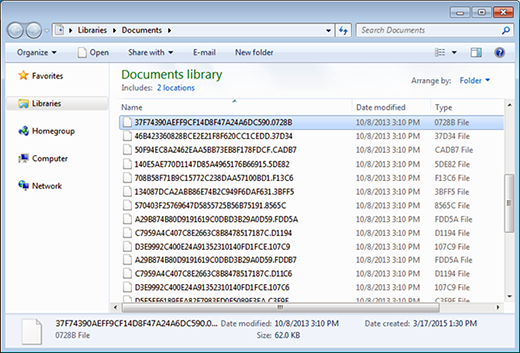
CryptXXX scours the infected PC and network shares for a range of file extensions that correspond to the most important user data. Subsequently, it encrypts all of these files, replaces the filenames with 32 hexadecimal characters and adds a random string like “.5DE82” in the tail. Since there is no way to open, edit or otherwise access these objects, the victim ends up studying the ransom instructions. More specifically, the full restoration of data is a matter of submitting $500, or 1.2 Bitcoin, during 100 hours since encryption. If the user exceeds this deadline, the size of the ransom will increase. Security labs and law enforcement agencies, including the FBI, advise that ransomware victims – both end users and companies – refrain from paying. Though the necessity to follow the criminals’ demands can be understandable in some cases, it’s strongly recommended to try alternative techniques first.
Automatic removal of RSA4096 virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download RSA4096 removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get RSA4096 automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files locked by the ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of RSA4096 virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.



