Table of Contents
A new 2016 version of the Cryptolocker virus is in rotation, leaving ‘Your files are locked !.txt’ ransom notes and providing email address for more instructions.
What is Cryptolocker virus?
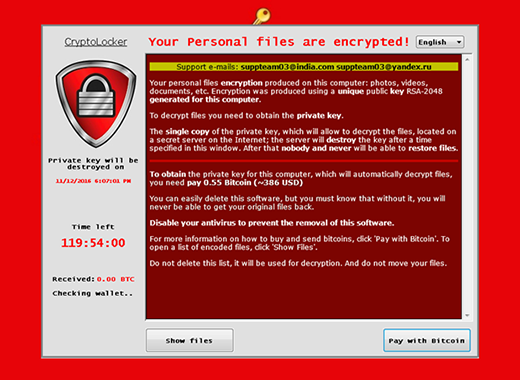
The cybercriminals engaging in today’s most nefarious rip-off scheme don’t seem to stop coining spinoffs of Cryptolocker, one of the earliest samples of file-encrypting ransomware. Its reputation, obviously, encourages crooks to follow suit and even dub their perpetrating products the same way. The latest contrivance in the range of these copycats is a Cryptolocker variant that creates ransom notes called “Your files are locked !.txt”. This user interface of this sample also contains a couple of support emails, which may include [email protected], [email protected], [email protected], or [email protected]. The ransomware pane also features a ticking timer that indicates the deadline for paying the ransom so that the victim’s files can be decrypted. Interestingly, filenames do not change as a result of this attack.
Researchers have labeled this particular strain as PClock. It intimidates the infected users with a warning that reads
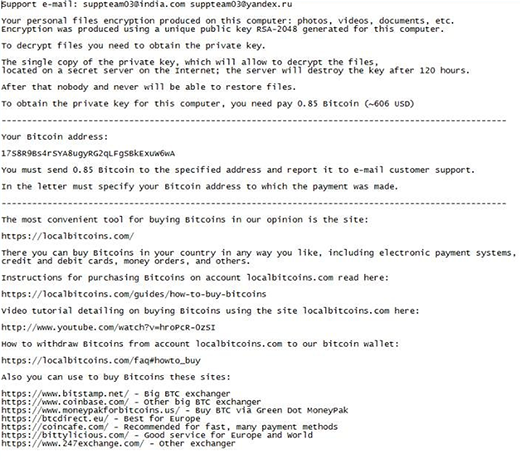
Your personal files encryption produced on this computer: photos, videos, documents, etc. Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt your files you need to obtain the private key.
Unfortunately, this alert does reflect the actually state of things. The new Cryptolocker 2016 leverages a strong asymmetric cryptosystem that cannot be cracked unless a unique private key is at the victim’s disposal. This chunk of data resides on the criminals-controlled server. So the compromise is certainly a huge predicament that results in the inaccessibility of an infected users’ personal data.
Computer users reportedly discover that their files have become locked after they visit their usual sites, including social networks, anime web pages and other resources providing streaming content. This fact points to a drive-by vector of the attacks. Most of the time, the would-be victims get persistent popups from the page they are on. This is a way to masquerade the malicious payload as if it were some routine request that needs authorization. In some cases, though, the ransomware arrives with spam. The attachments, which are disguised a payrolls, receipts, complaints and the like, evoke natural curiosity of the recipients. Once opened, they execute the infection.
Again, the criminals in charge of the updated Cryptolocker 2016 implement the cryptographic part of their attacks professionally. Therefore, experts have not found any algorithmic flaws as of yet, which means that data decryption isn’t possible unless the user has the relevant RSA key. The ransom walkthroughs explicated in “Your files are locked !.txt” documents tell the victim to submit 0.55-0.85 Bitcoin to their wallet. Then, the user is supposed to send an email to one of the support addresses in the ransom notes ([email protected], [email protected], [email protected], or [email protected]) in order to get further directions from the threat actors. Rather than start with this method, though, it’s recommended to try alternative techniques first. See below for details.
Automatic removal of Cryptolocker (Your files are locked !.txt) virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download Cryptolocker removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get Cryptolocker automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files ciphered by the Cryptolocker ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of Cryptolocker virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.




China government