Table of Contents
Get up-to-date information about the latest edition of the Crypt0L0cker ransomware and restore random 6-character extension files encrypted by this infection.
What is Crypt0L0cker ransomware?
Crypt0L0cker is one of the oldest copycats of the ransomware strain that came to denote file-encrypting malware as such. Its prototype called CryptoLocker is associated with the first major outbreak of this perpetrating software cluster in general. Discovered back in 2013, the infrastructure behind the original variant was dismantled in the course of a law enforcement effort dubbed Operation Tovar in May 2014. However, the malicious business model ended up moving on afterwards. The most harmful and widespread adherent of the bad craft was Crypt0L0cker, also known as TorrentLocker. Several iterations of this sample have been spotted in the wild over the past two years. One of them appended one’s files with the .encrypted extension, another one used the .enc string instead.
The most recent Crypt0L0cker campaign was unleashed in late November 2016. It’s steadily gaining momentum as of now. Having encoded personal files on a computer, the infection concatenates a random 6-character extension to every ciphered entry. The original filename and extension stay invariable, so the renaming algorithm returns a file structure like this: document.docx.nhewpz. In contrast to some of the prevalent ransomware specimens out there which completely scramble filenames, this onslaught doesn’t prevent victims from working out what items have been affected. Nevertheless, the data is encrypted with a military-grade cryptographic standard that doesn’t yield to commonplace recovery mechanisms.
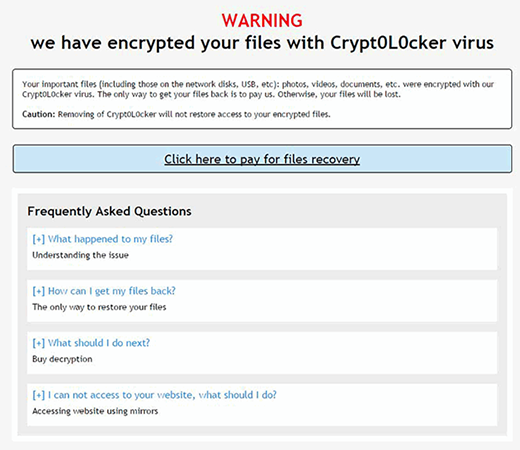
Crypt0L0cker leaves ransom notes called HOW_TO_RESTORE_FILES.html and HOW_TO_RESTORE_FILES.txt. The infected users won’t find it difficult to locate them as they will appear both on the desktop and inside encrypted paths on the machine. These manuals contain the following warning:
Warning
We have encrypted your files with Crypt0L0cker virus
– a really straightforward way to explain what happened. Their main objective, though, is to instruct victims how they can get their precious data back. Those contaminated are bound to literally buy the decryption for Bitcoins. The ransom is payable through a secret Tor (The Onion Router) page, with the URL being provided in the ransom notes. The recovery page indicates the amount of cryptocurrency for the buyout, which is typically somewhere between 0.5-1 BTC.
The way this crypto malady spreads is a no-brainer. The felons at the helm of the new campaign spawn numerous variants of spam emails to deliver the ransomware payload. Because these messages look like regular ISP notifications, invoices, newsletters or subscription cancellation requests, quite a few recipients get curious and open the malign attachments. This is an ambush that will get the unsuspecting user infected in no time. If Crypt0L0cker has sneaked its way into a PC, chances are the files will be restored via forensic techniques.
Automatic removal of Crypt0L0cker virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download Crypt0L0cker removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get Crypt0L0cker automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files ciphered by the Crypt0L0cker ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of Crypt0L0cker virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.