Table of Contents
The cybercrooks behind the Cerber ransomware have taken efforts to bolster their business, crafting an updated edition that appends the .cerber2 extension.
The newcomer to one of the most powerful ransomware campaigns inherits a lot of the same characteristics but also boasts quite a bit of uniqueness. The first striking difference is the “.cerber2” extension that replaced “.cerber” proper in the offending operational model. Secondly, the desktop wallpaper conveying the warning message after the attack is different, now mostly gray with numerous multi-color dots. Another enhancement has to do with the private crypto key, the size of which has increased two times up to 32 bytes. This particular tweak prevents researchers from breaking the encryption, although there hadn’t been much success in doing so with the previous variant anyway. The Cerber2 spinoff is distributed in the same ways, that is, through exploit kits and phishing. The latter vector is more widespread, though.
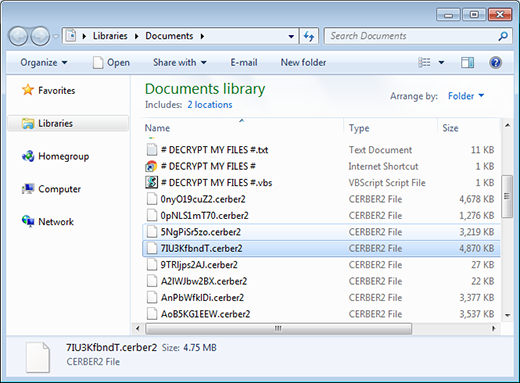
Having made its way on board a Windows computer in a stealthy manner, this ransom Trojan starts with searching for data. The machine’s hard disk, connected devices and network shares undergo a through scanning, in the course of which the virus juxtaposes the victim’s files against a list of extensions that’s incorporated in its code. This way, the infection is able to detect personal data as opposed to system components that are critical for the OS to run smooth. Then, it generates the AES encryption key and uses it to encode all items found during the scan. As a result, not only will the files’ data structure become scrambled, but their names will alter as well. In addition to concatenating the .cerber2 extension, the ransomware also replaces filenames with random gibberish strings of characters.
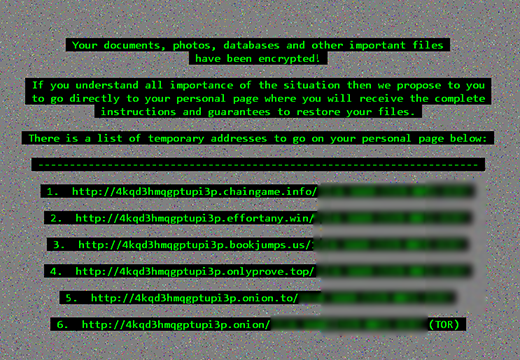
Then comes the phase where the Trojan straightforwardly tells the victim what happened and expresses its demands. To this end, it creates what’s called ransom notes, or documents with the entirety of recovery advice. Their names are the same as in the previous iteration: # DECRYPT MY FILES #.txt, # DECRYPT MY FILES #.html, and # DECRYPT MY FILES #.vbs. The text edition is opened with Notepad, the HTML one – with the default web browser, and the VBScript sample automatically plays an audio notification that says, “Your documents, photos, databases and other important files have been encrypted!”
Ultimately, the user is told to follow one of several Tor hyperlinks in order to visit their personal page named “Cerber Decryptor”. The page displays a timer that counts down 5 days, which is the period when a special price of the decryptor is valid. It amounts to 1.75 Bitcoin, or about $1000. Starting from day 6 onward, the price becomes 3.5 Bitcoin. Unfortunately, paying this ransom is the only viable way to obtain the decryption key at this point. Before giving up, though, it’s recommended to try a few tips and tricks that may work in some cases.
Automatic removal of Cerber2 virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download Cerber2 removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get Cerber2 automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files ciphered by Cerber2 ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of Cerber2 virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.



