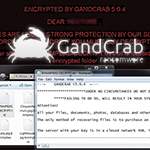
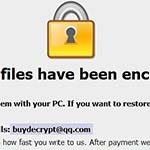
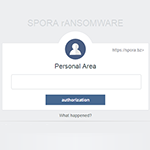
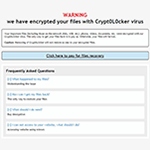
Decrypt and remove GandCrab 5.2 ransomware
Being infected with GandCrab 5.2 ransomware is beyond frustration – it’s a serious quandary that entails a denial of access to data and loathsome extortion. Most people who are more or less familiar with computer security have heard about ransomware. This despicable phenomenon has been a newsmaker for years. However, very few know the real … Read more