Table of Contents
Cerber3, the latest variant of a widespread defiant ransomware that plays an audio warning message to its victims, has started using the .cerber3 extension.
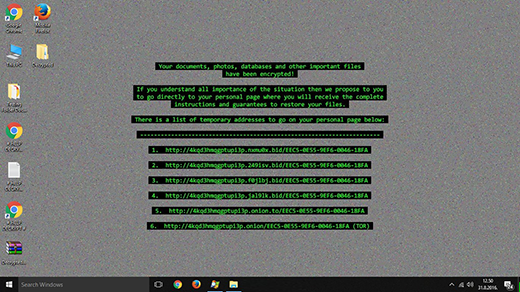
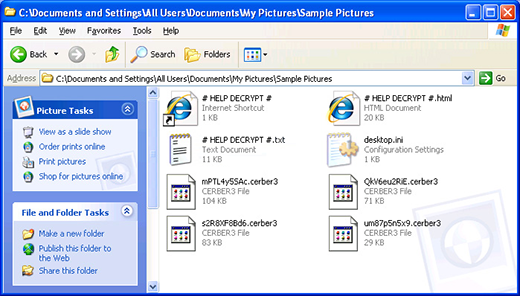
The file-encrypting threat generically dubbed Cerber has been invariably offbeat since it emerged. Its makers pioneered in utilizing .vbs files to literally pronounce their ransom demands via the infested PC’s speakers. While this feature has been preserved in the newest version of this infection, there are several noteworthy differences. First of all, the newcomer appends the .cerber3 extension to one’s personal files and jumbles filenames beyond recognition. For example, it transforms the name of a random document to a bizarre entry similar to uM87p3n3x6.cerber3. The files that contain steps to reinstate these messed up objects have also been modified. Now their names are # HELP DECRYPT #.html, # HELP DECRYPT #.url, and # HELP DECRYPT #.txt. A victim won’t find it hard to locate these ransom notes – they are created on the desktop and within all directories with ciphered data.
Just like its forerunners, Cerber3 is being deposited on computer systems by means of contagious email attachments or exploit kits. In the former case, a user receives an email with catchy contents and an enclosed JS file in a ZIP archive. Once you open the attached document, the ransomware gets inside undetected. When an exploit kit is in play, vulnerabilities in software that’s out of date are harnessed to inject the malicious loader. Regardless of the installation mode, the Trojan’s activity on a PC goes a uniform route across all incidents. It starts by running a scan for personal files stored on the local and removable drives as well as mapped and unmapped network shares.
The totality of data detected during the scan is subject to lightning-fast encoding. The Advanced Encryption Standard (AES) is the instrument that the perpetrators are banking on in this regard. This symmetric cryptosystem, if implemented the right way, is an insurmountable obstacle to recovery. Having completed the data encryption and filename scrambling part of its mission, Cerber3 generates a sinister audio alert, sets a new desktop background with some basic warning text, and drops the above-mentioned combo of # HELP DECRYPT # ransom instructions. From these documents, the victim will learn that they have to navigate to a Tor (The Onion Router) gateway. The Cerber Decryptor landing page provides the infected user with their personal restoration details, including the size of the ransom and the amount of time left before the fee will double. The original ransom valid during the first 5 days is 0.7154 BTC, or about $400. If the deadline condition isn’t met, it goes up to 1.4308 BTC.
Cerber3 ransomware attack is a tough-to-handle predicament. There is no free decryptor available for this strain. If paying up to the threat actors is an unacceptable option, be sure to try the tips below that reflect some potentially helpful forensic techniques.
Automatic removal of Cerber3 virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download Cerber3 removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get Cerber3 automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files ciphered by Cerber3 ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of Cerber3 virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.



Thanks,
This information helps the victim of the Cerber3 attack to decrypt his/her data/files.