Table of Contents
Learn how to handle the Spora ransomware, a sophisticated cyber adversary featuring a number of unique characteristics and a flawless extortion mechanism.
What is Spora ransomware?
In IT security terms, Spora has come to denote a violent file-encrypting ransomware. The name is a transliterated variant of a Russian word for “spore”. The conceptual ties are obvious for victims and malware researchers. The contagion is very toxic and it proliferates with a high infection rate. This malicious entity started spreading at the beginning of 2017 and has since taken root firmly enough to become one of today’s most harmful ransom Trojans. It arrives at Windows computers via a botnet that’s leveraged to generate massive spam waves. The files attached to these misleading emails pretend to be invoices, scanned copies of important documents, or similar subjects that recipients are likely to get interested in opening. In fact, the attachments are obfuscated HTA files that, once triggered, drop a JavaScript object into the Temp path of a targeted system. Then, another round of extraction results in firing a random-named executable.
Once this routine has launched the Spora ransomware, the infection does a tricky maneuver. While the process run by the malign EXE object is scouting the plagued workstation for important data behind the scenes, the victim will see a Microsoft Word file pop up out of the blue. This document displays a warning dialog stating that the file is corrupted. This is a clever move aimed at distracting the user from what’s actually going on in the background. In the meantime, Spora is looking for data types that correspond to popular formats, such as .jpg, .jpeg, .pdf, .sqlite, .doc, .docx, .xls, .xlsx, .rar, .zip, .rtf and a slew of others. Every such file is subject to encryption with a fusion of RSA and AES cryptographic algorithms. As a result, these data entries become inaccessible. Unlike many other ransomware programs out there, the Spora virus does not modify filenames as part of the data mutilation process – there are no extra extensions added, nor is anything prepended to the original names. And yet, the victim will quickly realize that their files got broken, because the infection leaves a ransom note and a .KEY file on the desktop.
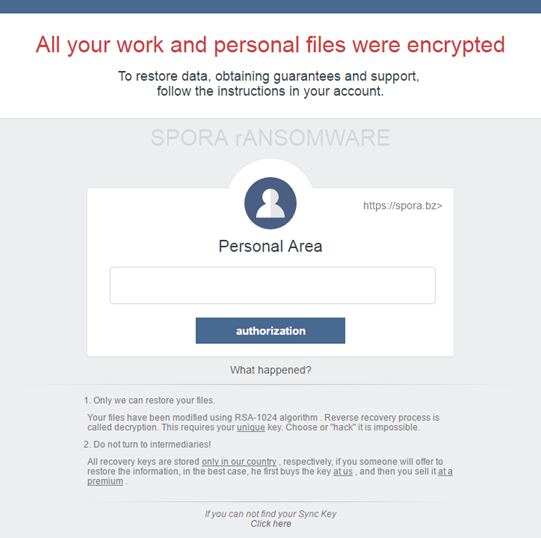
The decryption how-to is an HTML file whose name matches the victim ID. The latter is a unique string of 25 hexadecimal characters assigned to every contaminated computer. Having opened the ransom note, the user will be presented with a screen that says,
“All your work and personal files were encrypted
To restore data, obtaining guarantees and support,
follow the instructions in your account.”
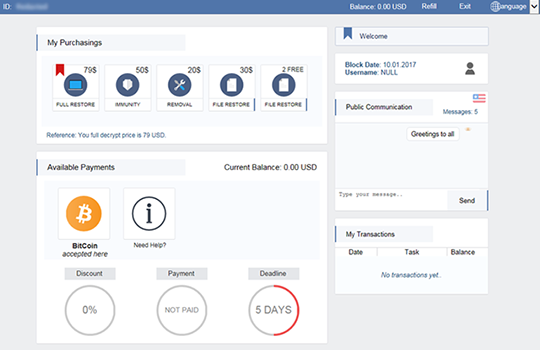
The window contains a Personal Area section (https://spora.bz or https://spora.biz), which requires that the victim enters the above-mentioned identifier to log into their Client Page. This page is a professionally tailored user console providing language selection, different data recovery plans, the option of restoring 2 files for free, a live support section, and up-to-date information on the current payment status. It’s too bad such a user-friendly dashboard serves such a nasty purpose.
Interestingly, the Spora ransomware collects certain types of user data and, based on that, puts every victim into one of six categories. Different ransom sizes apply to each of these clusters, so the infection will demand less money from a home user than it will from an organization. What is more, the threat actors deliver quality tech support. The agents are responsive and may even disable the ransom payment deadline if the infected user agrees to leave a positive review about the service. All in all, online extortion is getting worse in terms of technical complexity and interaction with victims. Unfortunately, there is no automatic decryptor to restore files locked down by the Spora ransomware. The good news is that there are specially crafted techniques that may do the trick for some of the ciphered files.
Automatic removal of Spora ransomware virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download Spora removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get Spora automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files ciphered by the Spora ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of Spora virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.