Table of Contents
The makers of the Djvu ransomware family continue to release new spinoffs of their harmful code, with the .masok file variant being the latest one on the list.
What is Masok ransomware?
Amidst the long-lasting hiatus in ransomware activity overall, some lineages continue to be active and still pose a serious risk to home users and businesses across the globe. The strain referred to as Djvu, or STOP ransomware, is one of the few that receive updates on a regular basis. It has recently expanded with a fresh remake that stains encrypted files with the .masok extension. It additionally creates a rescue note named _readme.txt, which is added to every folder with encoded information in it. Aside from the above-mentioned peculiar suffix, this infection does not alter the original filenames. Therefore, a random file Test.xlsx is renamed to Test.xlsx.masok. The pest uses symmetric AES-256 cryptographic standard to lock down the victim’s personal data. The crypto implementation is mostly flawless, therefore the odds of restoring the files are low unless the affected user has the decryption key.
Masok ransomware is typically distributed by means of spam. The extortionists are leveraging malicious properties of a botnet to send out misleading emails in bulk. These messages can be masqueraded as a receipt, job offer, CV, shipment arrival notification, or some other subject that’s likely to draw the recipient’s attention. These emails go with attachments in .zip, .docm, or .js format. When opened or extracted, these objects covertly download the ransom Trojan onto the computer. Once inside the host environment, the harmful code tries to disable VSS (Volume Shadow Copy Service) and then starts scanning the hard disk, removable drives (if any), and network shares for files that may be valuable to the victim. It focuses on personal documents, images, videos, and databases while ignoring system files which, if corrupted, might cause the system to malfunction.
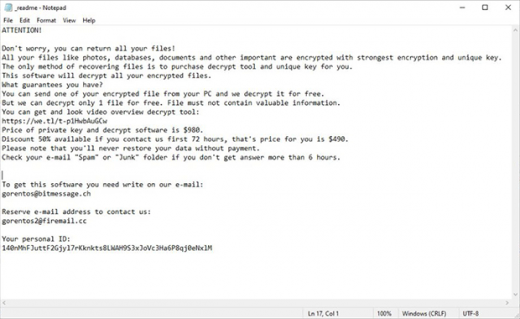
All the objects spotted in the course of the surreptitious scan are then encrypted. As it has been mentioned, the filenames get the .masok tail following the original extensions. By dropping the _readme.txt ransom message into all directories with ransomed data and onto the desktop, the pest explains what happened and explicates the techniques of reinstating the corrupted items. In particular, it says the victim has 72 hours to pay $490 worth of Bitcoin for the personal key and automatic decryptor. After this “grace period” expires, the ransom will double and amount to $980. In order to find out what BTC wallet the cryptocurrency should go to and how to proceed with the file restoration, the user is supposed to shoot a message to the attackers at [email protected] or [email protected] and paste their personal ID in it.
Here are a few things to consider in regards to the recommendations imposed by the cyber-miscreants. First of all, you can’t possibly be sure that they will follow through with their promises and provide the recovery toolkit after the payment is made. Even if they do, such a scenario is still a cold comfort.
Malware researchers claim the Djvu/STOP ransomware may be decryptable for free, but on a condition that an offline key was used to scramble your data. This could be because the contaminated machine wasn’t connected to the Internet during data encryption, or the crooks’ Command & Control server was down at that time. However, neither circumstance is very likely.
One way or another, this vector of recovery is certainly worth a shot. An application called STOPDecrypter is what does the trick as long as the above requirements are met. Go ahead and install it, let it scan your computer, and see if your case is supported. If the tool skips your files, it means that the Masok ransomware encrypted them using an online key and there is no effective way to restore them unless you opt for the criminals’ terms. With that said, it is strongly advised to start the DIY remediation of the adverse changes with the following steps.
Automatic removal of Masok ransomware virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download Masok removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get Masok automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover .masok files ciphered by the Djvu ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of Masok virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.