Table of Contents
With a large-scale outbreak of Akamaihd Mac virus being underway, there are methods to tackle the infection every victim should know about.
What is Akamaihd Mac virus?
Whereas browser takeover has always been a serious and annoying security issue, a recent boom in the Akamaihd Mac malware distribution has taken this phenomenon to the next level. This particular infection is a long-standing entity bolstering adware and malvertising campaigns for years, but it’s not until early 2020 that it has reached unprecedented heights and the trend appears to keep making itself felt consistently. The problem is all about virus-backed browser misconfiguration that entails multiple instances of traffic redirects via a URL with the a.akamaihd.net string in it.
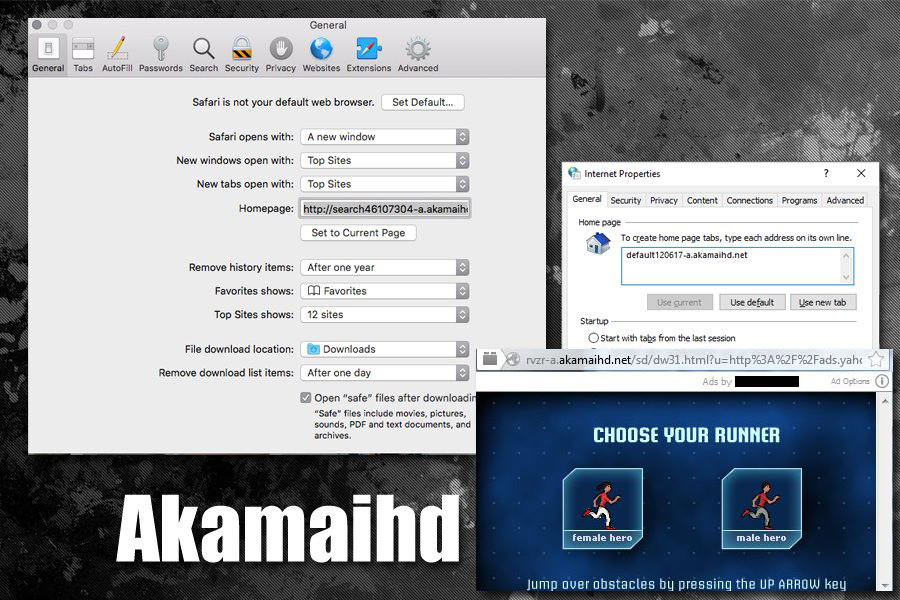
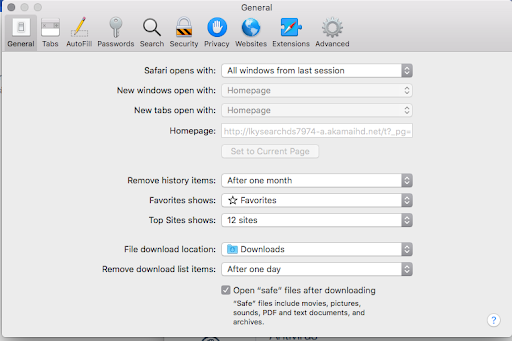
A few common variants of this nuisance involve domain names that appear in the following format: lkysearchds[random digits]-a.akamaihd.net, search[random digits]-a.akamaihd.net, or default[random digits]-a.akamaihd.net. Several real-world examples doing the rounds at the time of this writing are lkysearchds5927-a.akamaihd.net and search1173423-a.akamaihd.net. These strings replace the web browser defaults without any clear permission on the victim’s end. The affected settings include the homepage and search engine preferred by the user. As a result, Safari, Chrome, and Firefox iteratively resolve the wrong page on the contaminated Mac machine.
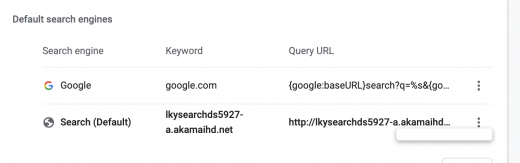
Although a specific variant of the akamaihd.net domain is listed in the malfunctioning browser’s customizations (see screenshot above), it’s not the one the affected user actually ends up visiting. This URL is an auxiliary link in a redirect chain that ultimately resolves another search provider. Although one of the landing sites dragged into this plot is the legit Yahoo Search, the hoax may also lead to known-malicious entities such as Search Pulse or Any Search. In the former course of events, the page under scrutiny plays the role of an intermediary resource dispatching the web navigation in such a way that it arrives at the trustworthy web service mentioned above.
This is an intricate tactic aimed at disguising outright malicious activity as something relatively benign. The primary goal of the malefactors is to tunnel the intercepted web traffic through a series of ad networks while making the whole ruse seem like a glitch with harmless search results at its core. Upon a little bit of closer inspection, though, the destination site turns out to be a custom Yahoo page whose header mentions Safe Finder, a dubious service that gained notoriety for being massively promoted by malware.
Contrary to the attack scenario revolving around the exploitation of Yahoo Search to instill a false sense of legitimacy, the akamaihd.net Mac virus can reroute the hijacked web browser to something clearly sketchy. For instance, the resulting pages can be search.searchpulse.net or search.anysearchmanager.com. Both are associated with infamous Mac browser hijacking campaigns run by a high-profile cybercriminal group. None of them returns authentic results of its own, simply operating as an ad-driven Internet traffic trading platform. It’s a shame that all of this profit making is being done at the expense of regular Mac users who fell victim to the browser-centered threat.
The propagation method that dominates the episode of modern cybercrime featuring the akamaihd virus is quite vanilla. It largely comes down to the fake Adobe Flash Player update stratagem involving deceptive popups shown on hacked or malicious websites. As controversial as it is in terms of gaping security loopholes, Adobe Flash is one of the things every user knows about. Therefore, a popup ad that recommends installing the latest version of this product to view some content online is likely to encourage a user to opt in. However, there are numerous trojanized variants of the application out there that disseminate Mac viruses in the same bundle. Therefore, it’s certainly a good idea to avoid installing such updates if they are pushed by intrusive alerts on websites. If the akamaihd infection is already wreaking havoc on a Mac, here are the steps that will help get rid of it.
Automatic removal of akamaihd.net virus from Mac
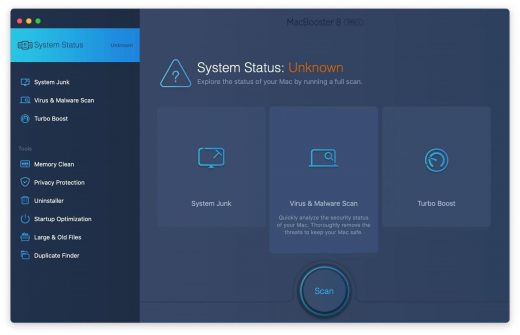
If this threat has infected your Mac, the most effective way to get rid of it is to use an automatic cleaning tool. The main benefit of taking this route is that the security application will accurately pinpoint and remove all the malicious files, including hidden components that could be difficult to find and erase manually. MacBooster is an award-winning solution that makes this process easy and fast. Follow the steps below to make the most of its malware removal and optimization power:
1. Download and install MacBooster onto your Mac.Download Akamaihd virus removal tool
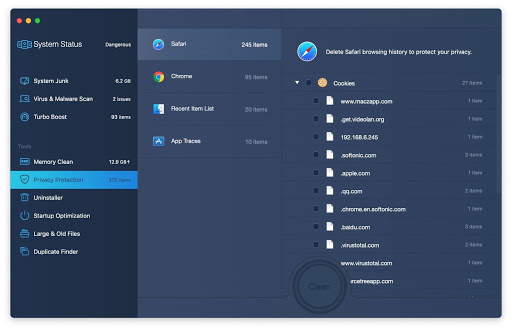
2. Open the tool and click on the Scan button on its home screen called System Status. The application will check your Mac for viruses and malware, memory issues, and junk files. 3. Once the scan is completed, MacBooster will display a report listing all the security and performance problems detected on your computer. Click on the Fix button to remove the malicious items and fine-tune your Mac’s performance.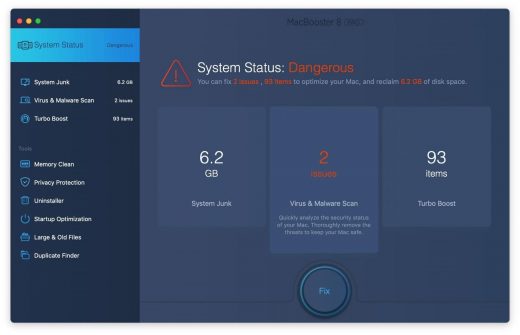 4. To address the after-effects of Akamaihd virus activity in the web browser, select the Privacy Protection feature in MacBooster sidebar, choose your default browser, and click on the
Clean button at the bottom. This will delete unwanted cookies and other items affecting the browser behavior.
4. To address the after-effects of Akamaihd virus activity in the web browser, select the Privacy Protection feature in MacBooster sidebar, choose your default browser, and click on the
Clean button at the bottom. This will delete unwanted cookies and other items affecting the browser behavior.
The Akamaihd virus shouldn’t be messing around with your Mac any longer. Be advised, though, that your default browser may still be redirected to dubious pages until you rectify its settings (the reset procedure will be described further down).
Akamaihd redirect virus manual removal from Mac
The gist of this section is to walk you through the process of deleting all non-obfuscated files related to the Akamaihd virus Mac. It’s best to perform the cleanup in the order specified below.
-
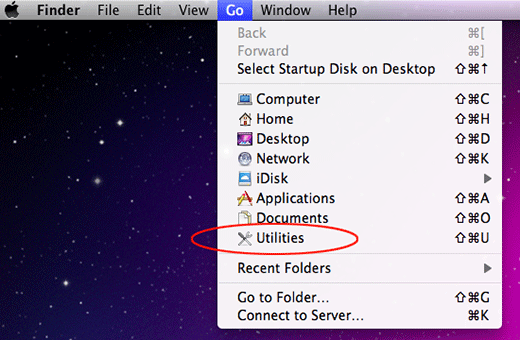
Click the Go icon in Finder and select Utilities on the list

-
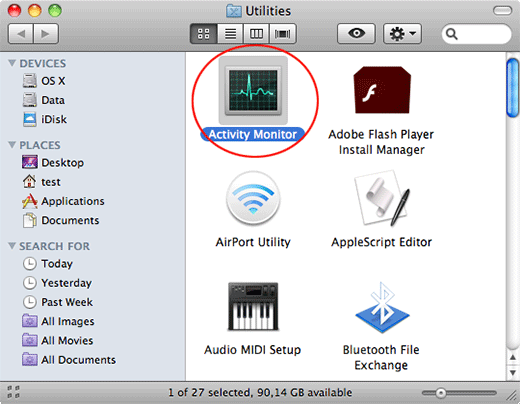
Find and select the Activity Monitor under Utilities

-
In the Activity Monitor, scrutinize the running processes for one that consumes lots of CPU and looks suspicious. Once the likely baddie is found, select it and click the Quit Process icon. An additional
confirmation dialog will pop up – click Force Quit on it

-
Now, go to Applications under the Go menu

-
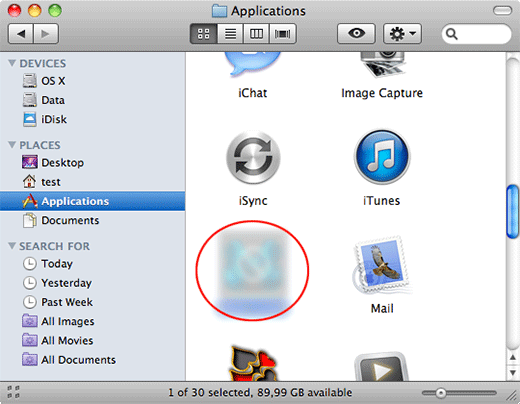
What you need to do is scroll down the list of installed apps in search of the malicious item. It could be a program with a gibberish name or one that ended up on your Mac beyond your awareness

-
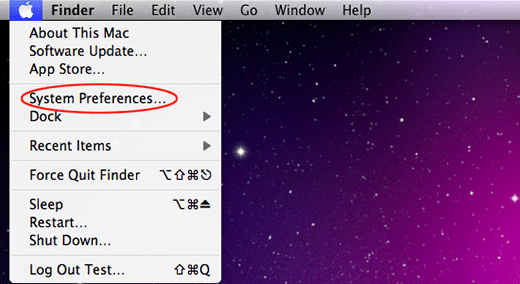
Go to System Preferences as shown below

-
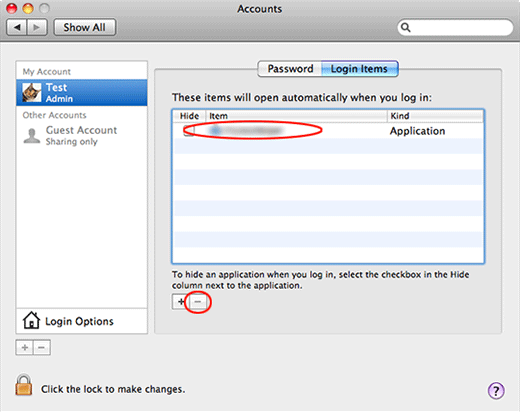
Select Accounts, then Login Items. You will see all the apps that run as part of the Mac startup process. Find the infection and remove it from the list by means of the “minus” icon

Now that you have suppressed the virus proper, you need to fix the problem in Safari. The browser defaults continue to be set to Akamaihd, therefore the repair requires some manual configuration tweaking.
Remove Akamaihd redirects from affected browser on Mac
The optimal troubleshooting method boils down to resetting the browser, which will undo all changes made by the infection or any third-party plugin without your permission. Here’s how to do it:
Reset Safari to its defaults
-
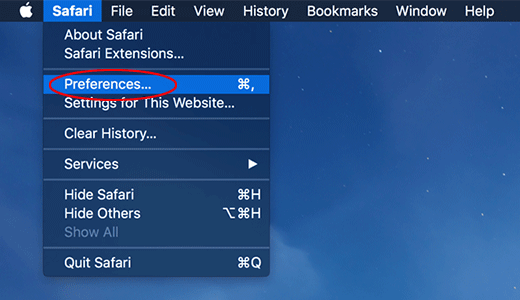
Go to Safari menu bar and select Preferences again on the drop-down list

-
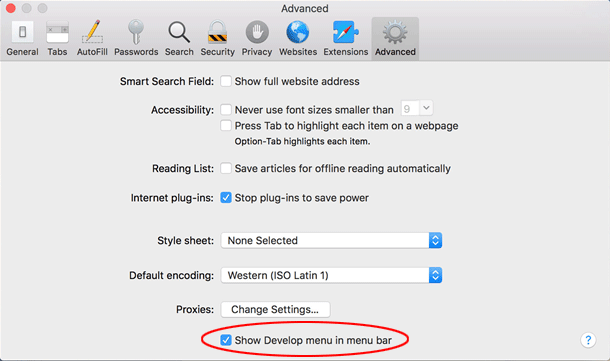
Go to Advanced tab and enable the option that says Show Develop menu in menu bar

-
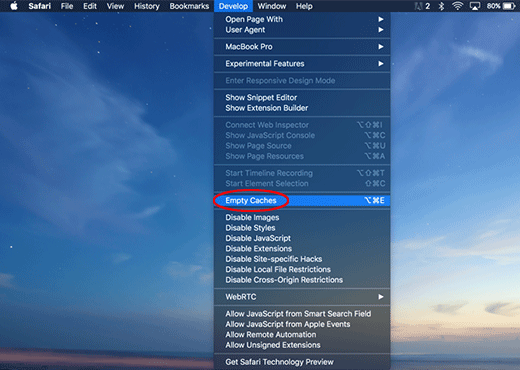
Now you will see the extra Develop menu in your Safari menu bar. Click it and select Empty Caches as shown below

-
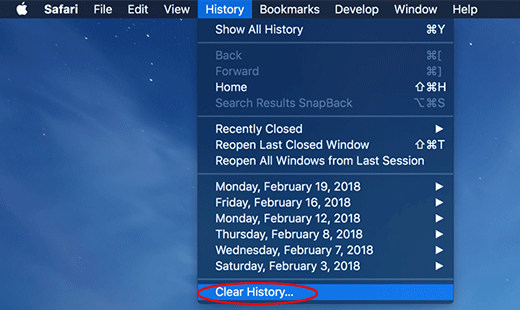
Do some test browsing to see if things are okay now and whether the malware is gone. If the issue is still there, you may need to additionally clear your browsing history in Safari. In Safari menu bar, select
History and click Clear History

-
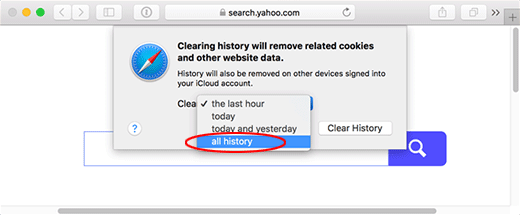
The browser will display a dialog so that you can select the required period you would like to clear history for. Select all history on the list and click the Clear History button

-
In case Safari is still acting up due to malware interference, there is one more thing you can try. Once again, go to Preferences from the Safari menu bar and select the Privacy tab
this time. Click Manage Website Data

-
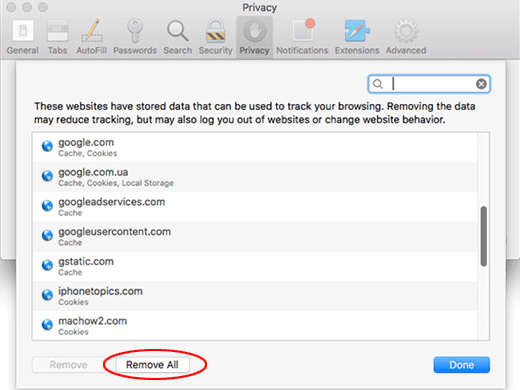
When Safari generates a full list of sites that have stored your browsing data, go ahead and click Remove All

- Confirm by hitting the Done button.
Reset Google Chrome
- Click More (⁝ icon) at the top right part of the Chrome window and select Settings
- Find the Advanced section on the Settings screen and expand it
-
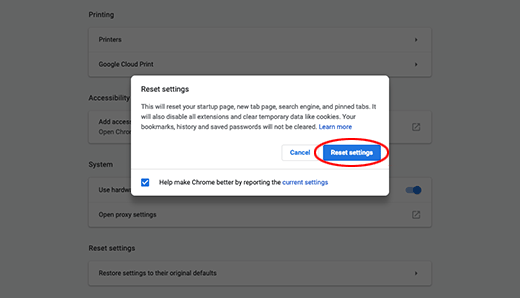
Locate the Reset settings subsection and click Restore settings to their original defaults

- Google Chrome will display a popup dialog asking you to confirm the reset. Click the Reset settings button on it. Now, restart the browser and ascertain that the problem has been fixed.
Refresh Mozilla Firefox
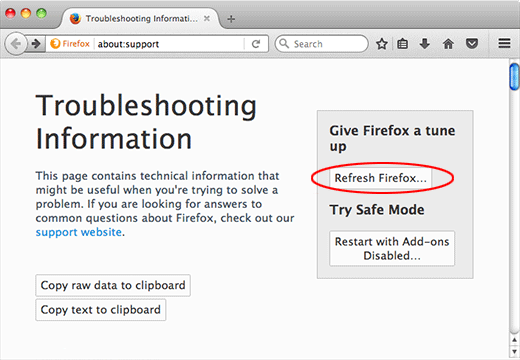
- Go to Help -> Troubleshooting Information, or type about:support in the Firefox URL bar
-
Once the Troubleshooting Information screen appears, find and click the Refresh Firefox button as shown

- Confirm the browser refresh on a dialog that will appear. Restart Firefox and check it for signs of malware tampering.