Table of Contents
Find out the connections between HELP_DECRYPT file and the vicious CryptoWall ransomware and learn how to get rid of the recurring popups at system boot time.
It’s not really a standalone computer issue that this article is going to highlight – instead, it’s more a symptom requiring urgent treatment in order to globally address a serious malware problem. The repeated encounters of a file named HELP_DECRYPT on a Windows PC ought to be interpreted as an unambiguous signal that a ransomware infection is currently residing inside the system and making a mess of one’s personal information. The genuine troublemaker in this scenario is called CryptoWall, which is a file encrypting virus that renders victim’s data impossible to open in a regular way. Any potential host machine is low-hanging fruit for this attack as long as the user practices poor security by, for instance, opening ZIP objects attached to suspicious emails. The ransomware has also been reportedly spreading by means of exploit kits, which are sophisticated tools that find and use software vulnerability based loopholes in one’s security.
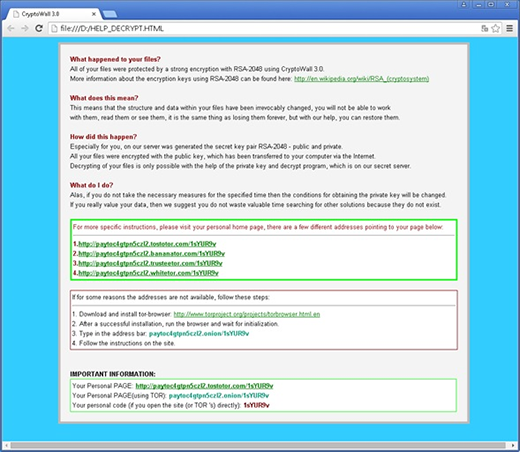
Unfortunately, the appearance of help_decrypt popup window after every computer startup means that the original virus has already done its nasty job, so it’s a post-factum fix that needs to be carried out. In other words, the actual ransomware has scanned all the letter-assigned hard drive sectors, found the files with popular extensions and encrypted them with RSA algorithm. By that time, it has also dropped the following files to each folder with encrypted items: help_decrypt.txt, help_decrypt.html, help_decrypt.png, and help_decrypt.url.
Because the malicious routine gets automatically added to the startup workflow, the help_decrypt window pops up whenever the machine boots. It contains general information about what happened to the user’s data and how to recover it. A number of victim-specific TOR links pointing to the dedicated “personal home page” are also provided in the file for the victim to proceed with the ransom payment amounting to a Bitcoin equivalent of 500 USD.
The CryptoWall contamination is too complex to completely handle via any single remediation vector. Technically, it’s not problematic to eradicate the ransomware itself, but that’s in no way related to the retrieval of encrypted personal files. The world’s leading security software vendors have been struggling to come up with a decrypt tool capable of recovering the data beyond ransom payment – to no avail at this point. The RSA standard leveraged in this attack presupposes generating a public and private key, one of which is stored on a remote C&C server controlled by the black hat hackers. Ultimately, the victims are bound to rely on chance while employing several workarounds, none of which is a panacea. The best-case scenario is if the user had maintained data backups, but regretfully that’s not the general practice nowadays. Please read the options below to keep help_decrypt window from popping up, remove the ransomware bug and try to make personal files accessible again.
Automatic removal of the CryptoWall virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download Help_decrypt removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get Help_decrypt automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files locked by the ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of Help_decrypt virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.



