Table of Contents
Get exhaustive details on the scenario where extensions of files on a PC are replaced with .ccc string and find out how to make the data accessible again.
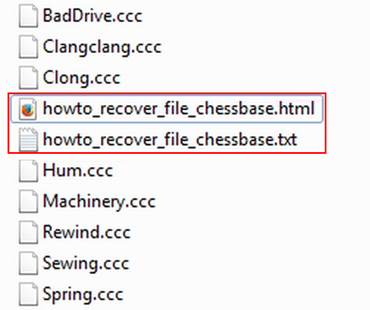
Symptoms of a ransomware assault depend on the trojan’s type as well as the gang distributing it. Though it certainly sounds strange, this filthy business has turned into an affiliate model where the creator of the virus might not even be involved in the spreading process. Interested parties can purchase the turnkey malicious service on underground resources, customize it and deliver the payload to computers. One of these rings has been pushing a version of the CryptoWall ransomware that assigns “.ccc” extension to the files it encrypted and displays ransom demands in a TXT or HTML document titled “howto_recover_file”. Be advised this is a sign of a specific build of the infection as CryptoWall is more commonly known to come up with Help_Decrypt ransom notes instead.
What this attack usually starts with is a new message appearing in one’s webmail inbox. It could look like a traffic rules violation notice, a delivery notification, a job offer, whatnot. The ZIP or PDF attachment to this email, when opened, will instantly execute the harmful process on the PC. The malware then scans all sections of the hard drive for data that matches a hard-coded extensions list. This way, it spots the victim’s personal files such as Microsoft Office docs, different image formats, videos and many more sorts of items that are likely to be important to the user. The RSA-2048 crypto routine implemented afterwards makes it impossible to open these files, moreover, the filenames are followed by .ccc string instead of the valid extensions.
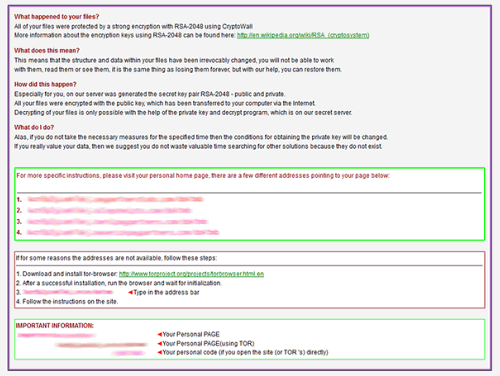
As mentioned, a document named “howto_recover_file” is created inside every directory that encompasses encoded information. Its HTML version will be automatically opened off and on, explaining what happened to your files and recommending the paid CryptoWall decrypt service to decode the data. All connections with the cyber-racketeers’ Command and Control server are established via The Onion Router, namely using the Tor Browser Bundle, so it’s highly anonymous all the way. The victims are required to pay in Bitcoins, which ensures an additional layer of anonymity and keeps the bad guys from being tracked down. Unless the payment deadline of 7 days is followed, the sum will increase.
RSA-2048 is not possible to crack, so the attacked user has two options: to pay the ransom or try the recovery methods below.
Automatic removal of the .ccc file extension virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download Howto_recover_file removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get Howto_recover_file automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover files locked by the ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of Howto_recover_file virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.