Table of Contents
Learn what malicious software tends to infect the Opera browser, be advised on ways to avoid the attacks and get instructions to remove this malware.
First and foremost, those who are questioning the popularity of Opera might change their mind after learning some bare facts about it. In late 2014, the overall user base of this web browser reached 350 million. Also, not every competitor can boast 24 years of background – Opera can. It has also been quite innovative throughout its history. Did you know, for instance, that it was the first browser to introduce the handy feature of graphical slots for quick access to favorite sites from a new tab? Major players on the market have followed suit and borrowed this functionality after Opera had pioneered with it back in 2007. So it’s a game changer in some aspects, plus it has earned quite a number of awards from authoritative resources such as PC World, About.com, and ZDNet.
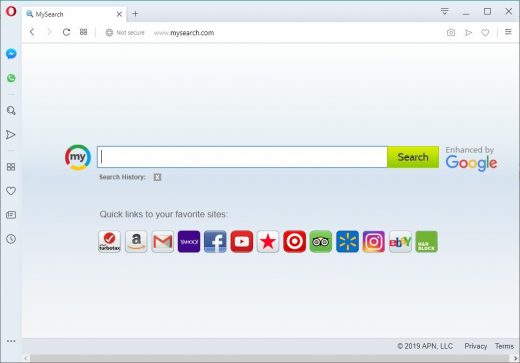
The web browser in question is hardly different from other widely used counterparts as far as virus attacks are concerned. The dominating variants of Opera malware include ad-supported PUPs (potentially unwanted programs) as well as homepage and search hijackers. Above is an illustration of a fairly run-of-the-mill malicious add-on in action. The user’s custom browsing settings, such as start page, preferred search engine and new tab site, are automatically modified by the infection, which is technically an extension that takes over critical privileges without being so authorized. The outcome is obvious: an unwanted web page will be constantly popping up instead of the user-defined URLs. This technique pursues the traffic redistribution objective, where interested parties pay the malware authors for capturing user hits.
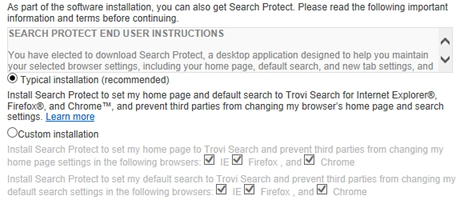
Luckily, Opera isn’t targeted by adware as much as IE, Chrome and Firefox are. The typical malicious code injection routine leveraged for infiltrating browsers is a tricky process that involves bundling with other software. In the course of this workflow, the user is expected to quickly click through dialogs that accompany the setup of the carrying freeware, the main idea being to make people fail noticing the indication of the unwanted promotion. Now, according to the analysis of these scenarios for some of the prevalent adware applications in the wild, Opera is sometimes not listed in such disclaimers (see image below). So, obviously, these threats aren’t quite cross-browser, which is good.
Another big cluster of Opera malware includes intrusive plugins that generate ads while the victim is surfing the web. Their distribution usually follows the same bundling pattern. In this case, the user will encounter multiple popup ads, comparison shopping boxes and in-text links across every web page that is visited. Interstitial ads are also likely to be triggered when the browser or new tabs are launched and whenever random space on sites is mouse-clicked.
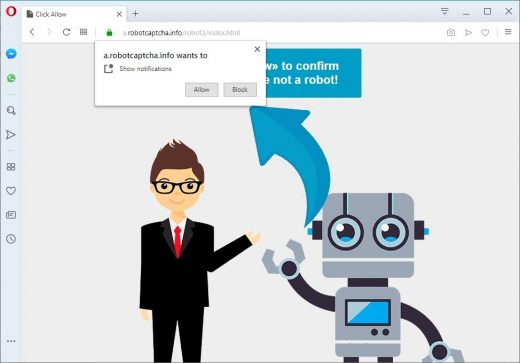
There is also an emerging scourge of Opera infections that try to dupe the users into allowing notifications for a particular sketchy purpose. In this scenario, the browser is repeatedly forwarded to a site that looks benign and may be masqueraded as a human verification page as shown in the following screenshot. The themes of such websites vary, but their goal is uniform – to brainwash the user into clicking the “Allow” button on a popup dialog. Although this may look like a garden-variety suggestion to stay tuned for news from a certain Internet source, the crooks end up exploiting the site notifications feature to deploy an irksome malvertising campaign in Opera. As a result, the victim will be redirected to numerous other pages containing sponsored or malicious content.
Regardless of the subcategory of malware that attacked your Opera browser, the cleanup tends to be more complex than the standard low-level troubleshooting. The adware may or may not be listed on Control Panel’s Add/Remove Programs interface. Even if it’s there, uninstalling it doesn’t necessarily lead to easy remediation of the adverse changes. Restoring the right preferences manually is hardly ever efficient either. The instructions below are an aggregate of the knowledge provided by security professionals in the context of eradicating viruses from Opera.
Techniques to remove malware from Opera
There are several vectors applicable to eradicate malicious code that ended up in your browser. Since both search hijackers and ad-inserting bugs tend to be embodied as malicious extensions or plugins, the first workaround is to uninstall these apps. While this approach is often efficient, sometimes it won’t work – it all depends on severity of a particular threat. In the worst case scenario, resetting Opera works flawlessly, but this procedure will erase all personalized browsing data. So try the former technique first, and if it doesn’t help, proceed to the latter (steps to be provided below).
Method 1: Manual removal of malicious components from Opera
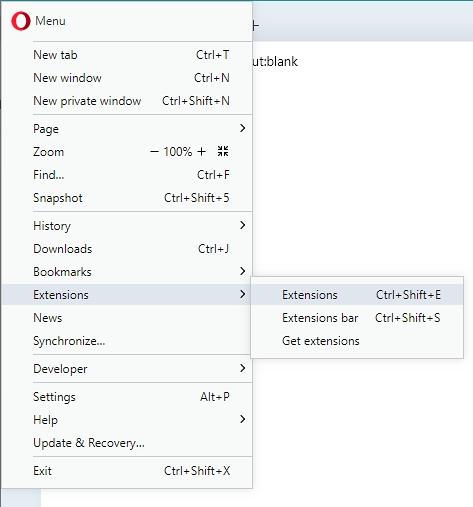
- Click the Customize and control Opera button in the top left-hand part of the window, select Extensions in the drop-down, and click Extensions in the expanded menu

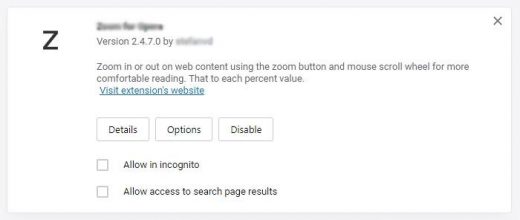
- Find the potentially harmful extension on the list and click Disable as shown below

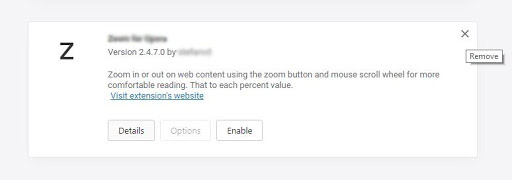
- Once the troublemaking extension has been disabled, go ahead and click the X button in the upper right-hand part of the screen section to remove it from Opera

- When a confirmation dialog pops up, click Remove to get rid of the extension completely

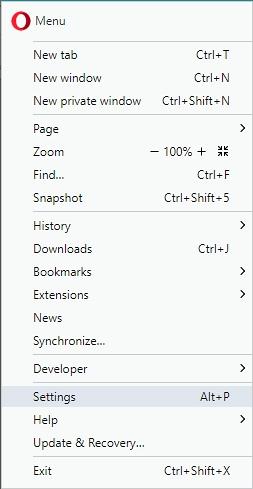
- Click the Customize and control Opera icon again and select Settings

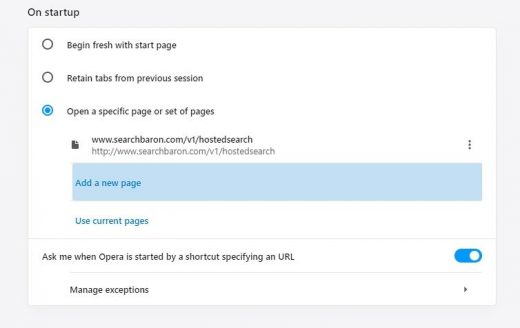
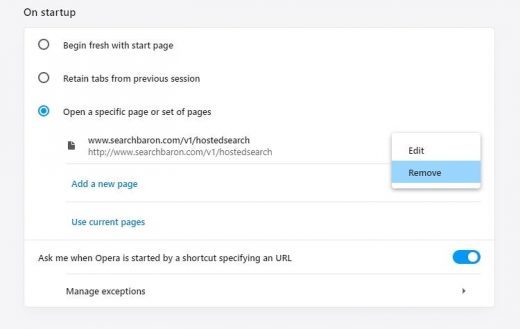
- Proceed to the section called On startup under Settings and select the radio button for Open a specific page or set of pages option

- Spot the unwanted homepage imposed by the malware, click More actions (⁝) icon next to it, and select the Remove option

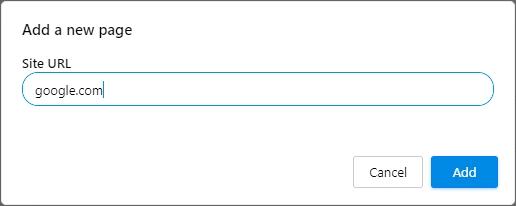
- Now pick the option saying Add a new page, enter the preferred start page, and click Add

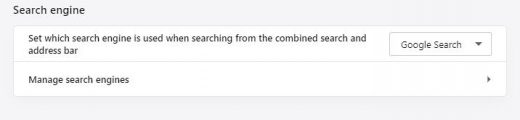
- Proceed to the Search engine section under Settings and select your preferred search engine on the list

- Restart Opera and browse around a bit to check if the problem has been fixed. If the symptoms aren’t occurring anymore, you’re good to go. In the event the issue persists, move on to the following troubleshooting vector.
Method 2: Reset Opera to its defaults
- Click Customize and control Opera and select Settings

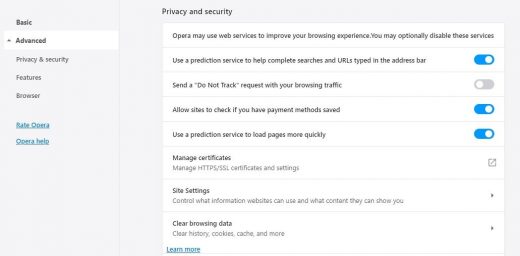
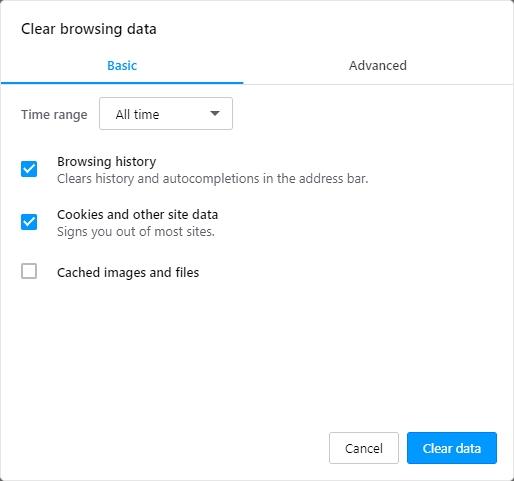
- Select the Advanced option in the left-hand part of the screen, go to Privacy & security, and click Clear browsing data

- When a dialog pops up, make sure all checkboxes are activated, select All time in the Time range drop-down list, and click Clear data at the bottom

- You are done resetting Opera. Do some test browsing to see if things are okay now and whether the malware is gone.
Verify whether the virus has been completely removed from Opera
Computer threats like the Opera malware virus can be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.



thanks it works
I have tried it many times and there is still malware. What can I do now?
elly,
Try booting into Safe Mode by repeatedly tapping F8 key during computer startup. Then, follow the tips covered in this tutorial.
Regards
So many thanks…!!!
It works…
Thank you for the great article
This is actually helpful, thanks.