Table of Contents
Read about the typical schemes used by malware to attack Internet Explorer and learn how to address the contamination of this sort in several steps.
None of the present-day top web browsers compares to Internet Explorer in terms of the history. It was released in 1995, so it’s truly an old stager that was live long before the contemporary competitors even existed. The 20 years of background have been controversial at times, and yet IE definitely deserves a respectful attitude regardless. Security-savvy users are well aware of the caveats pertaining to this browser, including mostly the vulnerabilities that Microsoft would often fail to patch on time. These loopholes have exposed this piece of software to newsmaking zero-day attacks multiple times. Despite this, according to NetMarketShare, different versions of Internet Explorer are used on about 40% of desktop computers. Perhaps these statistics might be somewhat blurred due to this product’s distinguishing feature, namely that it is built into Windows operating systems without the option to uninstall. Anyway, the fact that IE is quite popular and its potential security shortcomings make attackers continuously put their mind to exploiting it.
Cybercriminals predominantly focus on injecting malicious apps called “adware” into Internet Explorer. The name of this malware category is quite self-explanatory: it denotes unwanted entities which are designed to display ads as the victim is surfing the web. Adware threats are usually impersonated as browser helper objects and plugins, and their moderate severity allows the fraudsters to evade prosecution in most cases. In the meanwhile, rerouting the victim’s web traffic to pages filled with sponsored entries or inserting those directly into websites makes it easy and fast for the black hat hackers to get the bang for their buck.
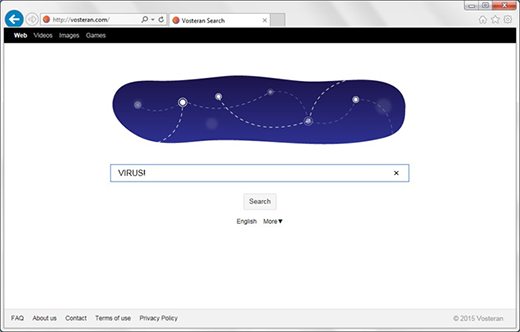
The adware subcategory which meddles with one’s IE preferences is on the rise. Also referred to as homepage and search hijackers, these viruses make you repeatedly visit spoof search engines. When a random query is typed in these websites, the results will include advertisements along with the few relevant entries. This adverse activity is typically powered by a malicious add-on that automatically replaces the user-defined custom settings with a different URL, so the values for homepage, new tab page and default search get distorted. The particularly abominable thing about this interference is it bypasses authorization by the user.
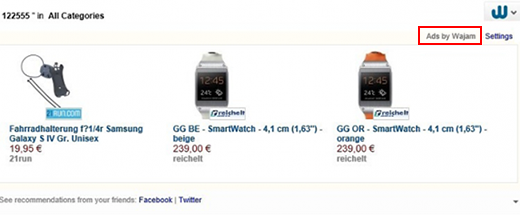
No less annoying and disruptive are the infections that embed different types of ads into the sites that the victim visits via Internet Explorer. The redundant advertisements may appear above search results, on social networking services and inside the layout of regular web pages such as blogs, news sites, etc. The user will keep bumping into large banners with information about various goods, price comparisons, coupon boxes and questionable app download offers. When the victim clicks anywhere on a page, even on blank parts of it, interstitial pages might pop up out of the blue. To top it off, some words become clickable due to added hyperlinks that redirect you to a sponsored page.
Most categories of IE malware are distributed through software wrapping, or bundling, technique. This methodology creates an illusion of user consent to install something, while in fact people hardly ever notice the complementary items that are incorporated into the setup. Freeware programs such as video downloaders or format converters are the main disseminators of adware infections. Sometimes you can opt out (see image below), but not always.
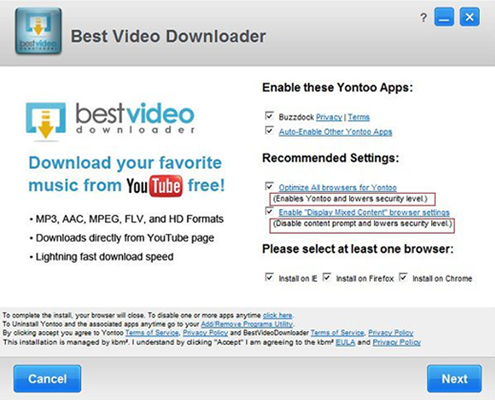
It’s hard to judge the validity of the stereotype that Internet Explorer isn’t too secure, because other browsers get attacked by malware on a large scale as well. The overwhelming majority of contamination occurrences take place due to the users’ low security awareness and lack of caution when installing new software. If a malicious app has compromised IE on your computer, use the instructions below to get rid of the pest.
Techniques to remove malware from Internet Explorer
There are several vectors applicable to eradicate malicious code that ended up in your browser. Since both search hijackers and ad-inserting bugs tend to be embodied as malicious extensions or plugins, the first workaround is to uninstall these apps. While this approach is often efficient, sometimes it won’t work – it all depends on severity of a particular threat. In the worst case scenario, resetting IE works flawlessly, but this procedure will erase all personalized browsing data. So try the former technique first, and if it doesn’t help, proceed to the latter (steps to be provided below).
Method 1: Manual removal of malicious components from Internet Explorer
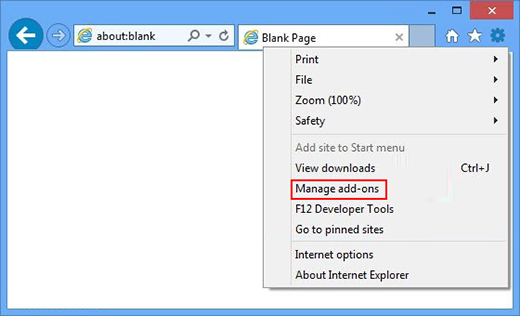
- In IE, go to Tools and choose Manage add-ons option in the drop-down menu

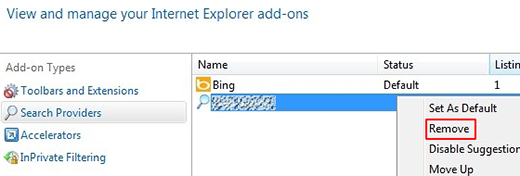
- Select Search Providers in the left-hand part of the interface. In the field to the right, choose the preferred search engine and select Set as default option. Also, click on the malicious entry with your mouse and remove it from the list

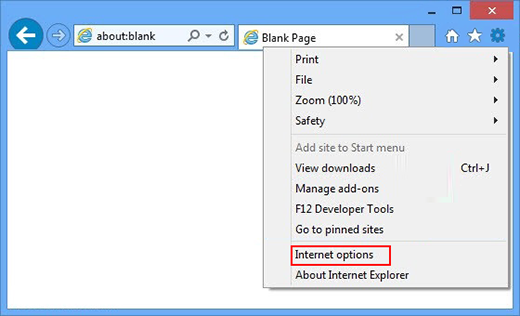
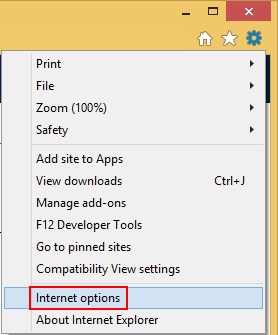
- Now go to Tools and choose Internet Options

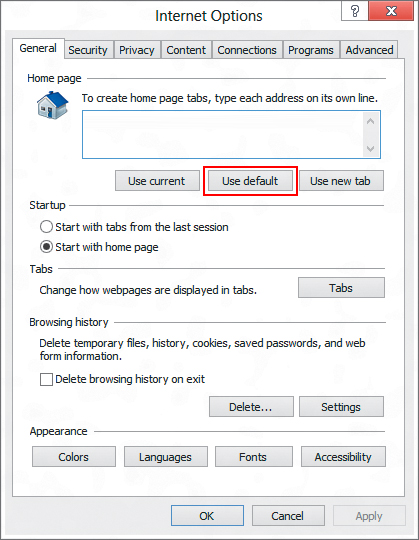
- Hit the General tab and click Use default option or type in the homepage you would like to open at browser launch

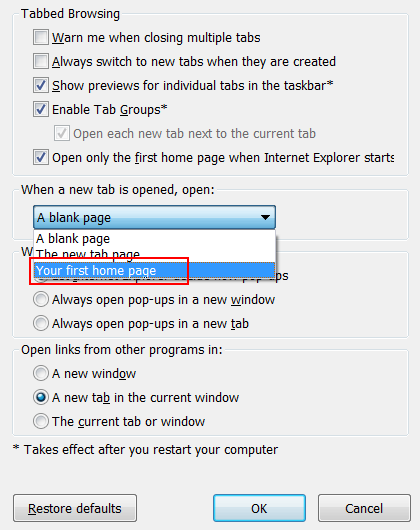
- Click the Tabs button on the same screen

- As shown on the screenshot below, select A blank page or Your first home page on the list. Hit OK to save the changes

- Restart IE and browse around a bit to check if the problem has been fixed. If the symptoms aren’t occurring anymore, you’re good to go. In the event the issue persists, move on to the next troubleshooting vector.
Method 2: Reset Internet Explorer to its original state
- Go to Tools and select Internet Options from the list

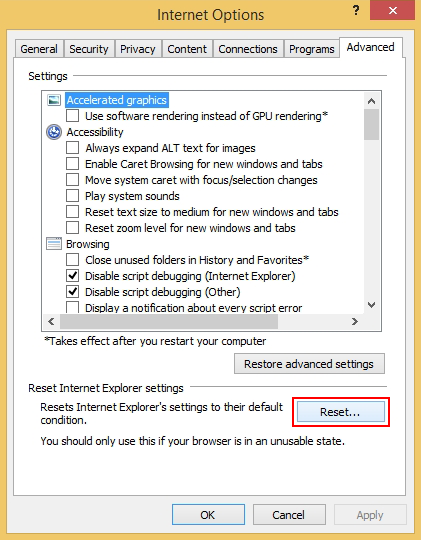
- Hit the Advanced tab and click on the Reset option

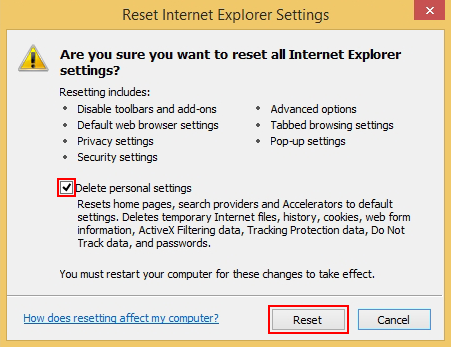
- IE will now display Reset Internet Explorer Settings box, where you should put a checkmark next to Delete personal settings option and click Reset at the bottom

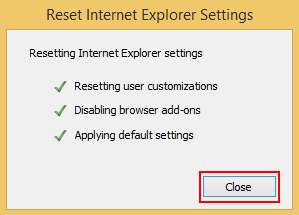
- Click Close on the reset status popup

- Restart your computer so that the changes can take effect
- Do some test browsing to see if things are okay now and whether the malware is gone.
Verify whether the virus has been completely removed from IE
Computer threats like the Internet Explorer malware virus can be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.
Download Internet Explorer malware virus scanner and remover