Table of Contents
Be instructed on methods to get rid of malware in Chrome, review the common symptoms of this kind of infection, and learn some basic virus prevention tips.
Chrome is designed to be fast, safe and easy. These indisputable benefits as well as the vendor’s reputation have enabled the product to quickly catch up to its main competitors and become the world’s most popular web browser since the initial release back in 2008. Popularity of any software, however, makes ill-disposed individuals put their mind to ways of exploiting it, because the bigger a potential attack surface the more productive it is for illegal profit gain.
Google is generally known for taking security seriously, so the browser is a moving target that cannot be easily compromised. This is why cyber fraudsters are leveraging unethical practices to get their code delivered to targeted computers and installed in Chrome. In other words, most of the viruses tailored to hit it end up there because the users actually authorize these bugs to get in. The trickery is about whether or not people realize it, which they mainly don’t. Different types of social engineering, including phishing, often become a springboard for a compromise. The primary vector of contamination at this time is what’s called “bundling”, which denotes a framework where the user gets owned while installing other applications. Those are open source tools whose installation can only be completed if you opt into the extra that they go with.
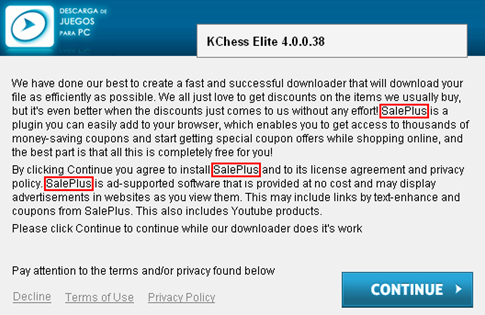
For you to get a better idea of the most widespread types of Chrome malware, let’s look into a few samples: one for the so-called search and homepage hijacker, and the other for the ad-injecting subcategory. The spreading workflow for both is clearly demonstrated by the screenshot above, where a third-party applet promotes the harmful payload in the way that the user might not even notice the hoax.
SalePlus exemplifies the infections that embed redundant advertisements into the layout of visited sites. Again, it is distributed in tandem with affiliated freeware products. Once this adware has infected a computer, it adds a new plugin or object masqueraded as a web service enhancement. The user is not involved in the process of authorizing the program to make changes to the browser’s functioning and get admin-level privileges.
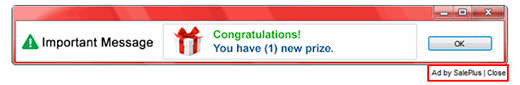
Consequently, the virus inserts ads into every web page, for instance comparison shopping sections, freebies, coupons, in-text links, etc. This is a model based on pay-per-click and pay-per-view advertising. It’s too bad that it gets deployed in contradiction with the user’s interests. The victim’s privacy is at risk too, because personally identifiable web browsing information is collected by the app and can be handed over to third parties.
Another widespread species of Chrome viruses is represented by apps like Binkiland, or WSE_Binkiland, which is generically classified as adware. Its technical background is as follows: it operates as an extension which modifies Chrome’s homepage, default search, new tab and shortcut settings without requesting user approval. These changes are highly persistent, so attempts to reconfigure the browsing preferences manually are infrequently actionable.
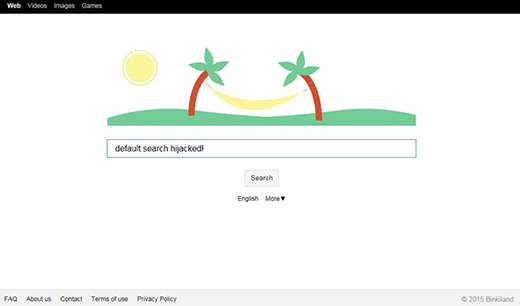
Through a technique as intrusive and abominable as that, the adware forces you to use its own landing page, which is a search service with a lot of ads above the fold on its results pages. These sorts of sites are typically safe to visit, but the fact that they are imposed on you by someone else isn’t comforting at all.
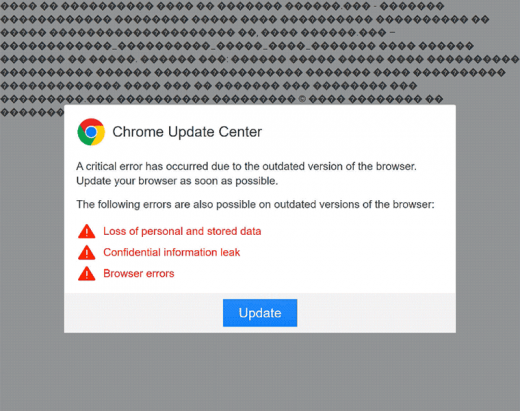
A peculiar vector of attacks tainting Chrome has to do with deceptive popups that feign urgency regarding a browser update. To orchestrate this hoax, cybercriminals may follow two routes: depositing dodgy ads on hacked or disreputable websites; or spreading a browser-hijacking PUA (potentially unwanted application) under the guise of useful freeware. Either way, the user is going to be redirected to a scam web page that shows a phony “Chrome Update Center” popup notification. This alert says a critical error has been encountered due to outdated version of Chrome and lists a few scary-looking adverse effects to hoodwink the victim into opting for the recommendation. However, by applying this pseudo update, the user actually agrees to install another malware. It could be a ransomware infection, spyware, banking Trojan, or stealthy cryptominer. This incursion fits the mold of stratagems with a flavor of social engineering, which are so common in the Chrome exploitation climate.
Widespread tech support scams bear a resemblance to the above technique as they try to persuade the victims that there is something critically wrong with their computers, only to fool them into contacting a rogue technician. In the aftermath of this manipulation, Chrome users run the risk of allowing the scammers to access their systems remotely and install something harmful under the pretense of troubleshooting.
Chrome is definitely not a low-hanging fruit to attackers as Google, thankfully, does invest heavily into security. In case you have been tricked into installing something that messes up your browsing, however, be sure to read the recommendations below and fix the problem in several steps.
Techniques to remove malware from Chrome
There are several vectors applicable to eradicate malicious code that ended up in your browser. Since both search hijackers and ad-inserting bugs tend to be embodied as malicious extensions or plugins, the first workaround is to uninstall these apps. While this approach is often efficient, sometimes it won’t work – it all depends on severity of a particular threat. In the worst case scenario, resetting Chrome works flawlessly, but this procedure will erase all personalized browsing data. So try the former technique first, and if it doesn’t help, proceed to the latter (steps to be provided below).
Method 1: Manual removal of malicious components from Chrome
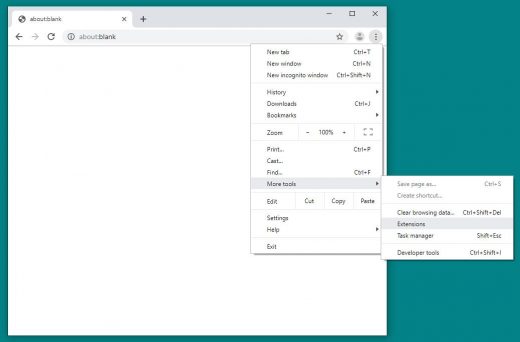
- Click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the Chrome window and go to More tools –> Extensions

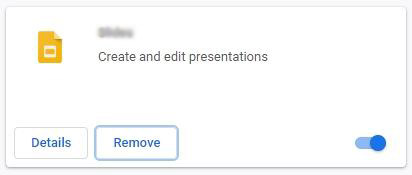
- Find the potentially malicious extension on the list and click Remove

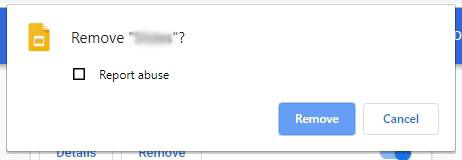
- On a confirmation dialog that will appear, click the Remove button again. This will eliminate the unwanted item from Chrome

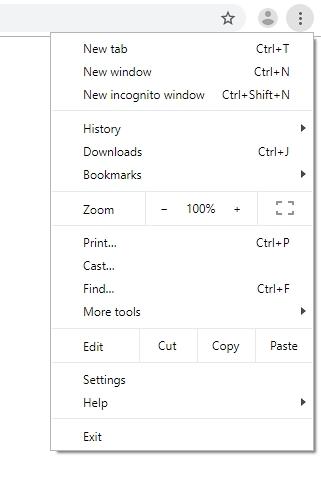
- Click the Customize and control Google Chrome (⁝) icon again and select Settings

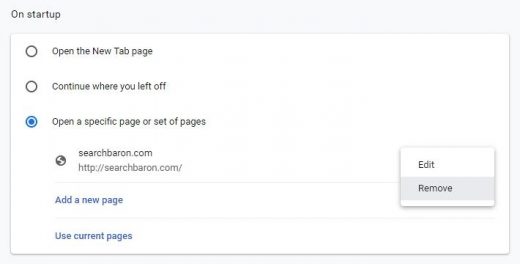
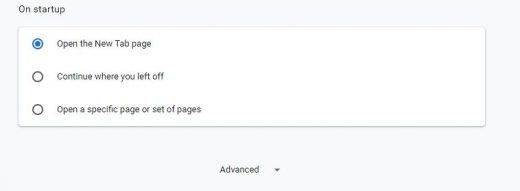
- Proceed to the section called On startup under Settings, select the radio button for Open a specific page or set of pages option, and spot the unwanted homepage URL there (if any). Click the More actions (⁝) icon next to it and select Remove

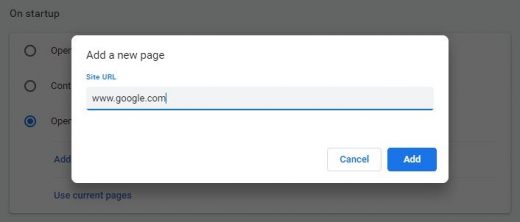
- Click the Add a new page option, enter the preferred homepage URL in the dialog that pops up, and click Add

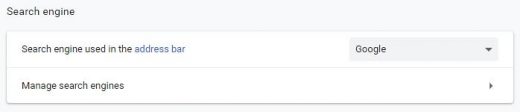
- Proceed to the Search engine section under Settings and select the search engine that will be used in Chrome’s omnibox (address bar)

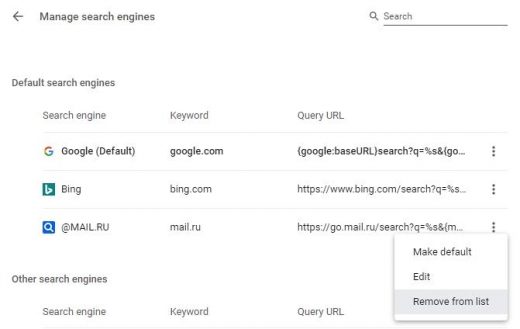
- Now, go to Manage search engines, find the unwanted search provider on the Default search engines list, click More actions (⁝) icon next to it, and select Remove from list option

- Restart Chrome and browse around a bit to check if the problem has been fixed. If the symptoms aren’t occurring anymore, you’re good to go. In the event the issue persists, move on to the next troubleshooting vector.
Method 2: Reset Chrome to its original state
- Click the Customize and control Google Chrome (⁝) icon as shown on the image and select Settings

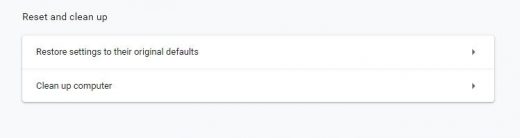
- Scroll down the Settings screen, find and click the Advanced option

- Under Reset and clean up section, hit the Restore settings to their original defaults button

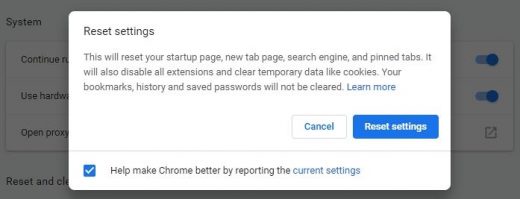
- On the warning that popped up, read everything you should know about the consequences of the reset. Click Reset settings if you want to complete the procedure

- Restart Chrome for the changes to take effect. Also, do some test browsing to see if things are okay now and whether the malware is gone.
Verify whether the virus has been completely removed from Chrome
Computer threats like the Chrome malware virus can be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.