Table of Contents
Files with .zzzzz extension are inaccessible because they are encrypted by the latest version of the Locky ransomware, which requests Bitcoins for decryption.
What is .zzzzz file ransomware?
It’s difficult to question the usefulness of cryptography. It has numerous benign applications in the realm of safeguarding sensitive data. The evolution of malicious software, however, caused this conventional state of things to turn upside down. When the scourge of ransomware emerged on the computer threats arena, it became obvious that the inherent strength of cryptographic algorithms had the evil potential to wreak havoc with users’ proprietary files rather than protect them. One of the data-encrypting hoaxes called Locky has become a buzzword that denotes an uncrackable ransomware on steroids. This family tends to continuously mutate, with distinct tweaks being made to its code and activity patterns every so often. In the course of the most recent update, Locky has assumed the form of a crypto infection that adds the .zzzzz extension to one’s files and drops the -INSTRUCTION.html and -INSTRUCTION.bmp ransom notes.
The way the Locky/zzzzz ransomware infiltrates computers isn’t a matter of reinventing the wheel. Its operators are really good at social engineering, so they opt for a payload distribution tactic that relies entirely on human curiosity and gullibility. The carrier of the contagion is spam that delivers a ZIP archive with a malicious JavaScript file inside. The bad guys may disguise this attachment as a spam mailout log detailing the alleged offending activity from the recipient’s email account. There are other themes of these tricky messages, including bogus local company representation offers, CVs, receipts, invoices, paychecks and the like. A standalone campaign is being currently conducted via Facebook, where users receive a malware-tainted .svg photo that downloads the crypto baddie when opened.
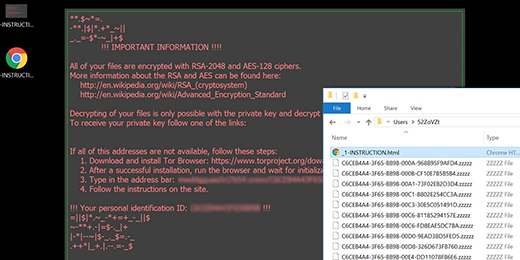
The Zzzzz virus literally fleets across a computer once the compromise has taken place. It scans the hard drive, removable media and all cloud drives for hundreds of data formats in order to locate the entries that matter to the victim the most. All files that match the ransomware’s built-in whitelist of targeted extensions then become crippled through the use of two different cryptosystems. The virus utilizes the RSA-2048 and AES-128 standards to make it impossible for the user to open, edit or otherwise process their personal files. On the outside, the changes are drastic as well: filenames get substituted with weird-looking lines of 32 hexadecimal chars suffixed by .zzzzz.
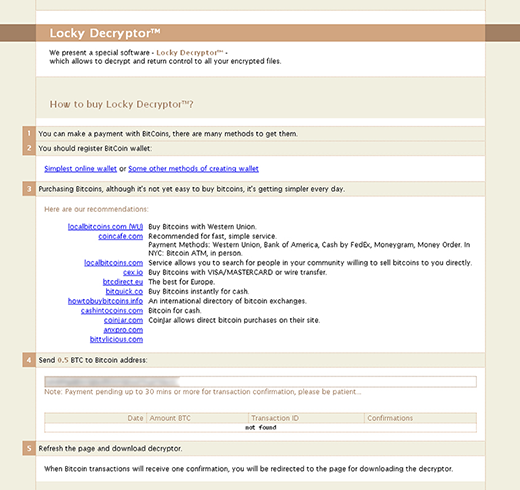
The ransomware creates the aforementioned -INSTRUCTION.html and -INSTRUCTION.bmp files on the desktop to tell the victim what they must do to decrypt their information. Additionally, a document named _[random_digits]-INSTRUCTION.html will be dropped into encrypted folders. According to these manuals, the user is supposed to download and install the Tor Browser bundle, copy and paste their personal recovery link into this anonymous web navigation client, and then follow the steps listed on the site called Locky Decryptor. In a nutshell, the buyout deal implies paying 0.5 Bitcoin to a specified cryptocurrency wallet and then downloading the automatic decryption software. No one can guarantee that the procedure will be as smooth as this, so think twice before submitting the money to the attackers. Try a few workarounds instead (see below). The applicable restoration methods revolve around forensic tools and file snapshots made by Windows earlier.
Automatic removal of the .zzzzz virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download .zzzzz removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get .zzzzz automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover .zzzzz files ciphered by the ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of .zzzzz virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.