Table of Contents
Learn how to minimize the risk when infected with the .crypted file extension virus and what can be done to restore the encrypted data beyond the ransom route.
Whereas the family of crypto lockers called Nemucod doesn’t exhibit any offbeat or particularly high-profile characteristics, the danger emanating from it should not be underestimated. The principal attribute that makes a random piece of ransomware successful is the correctness of implementing the cryptographic part of its modus operandi. The .crypted file extension variant of Nemucod is immaculate in this context. It efficiently leverages the RSA-1024 algorithm to prevent contaminated users from accessing their personal files. Under the circumstances, the only way to unscramble the data is to get hold of the private RSA key. The threat actors who own this key offer the victims to purchase it for 0.39 Bitcoins, which is equivalent to 240 USD at the time of writing. Consequently, a targeted person has to somehow deal with a bevy of inaccessible files with the .crypted string following the original filename and extension.
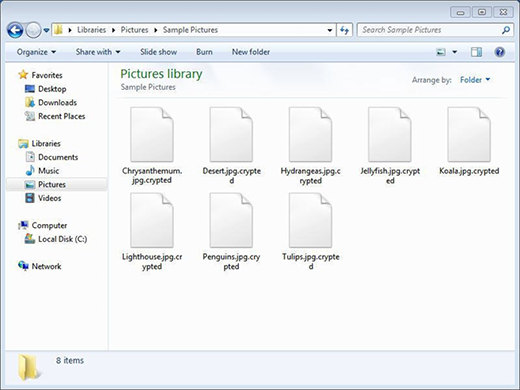
Speaking of the contamination process, it is trivial by its essence but has a considerable conversion rate. The entities to look out for are files attached to spam. Cybercrooks engaging in online extortion contrive ways to generate big email volumes, where the messages are rogue payroll reports, invoices, traffic violation notifications, curriculum vitae documents or similar. As soon as an unsuspecting recipient double-clicks on the attachment, the execution of .crypted virus on the computer is a matter of seconds. The infection then traverses the local, removable and network-based drives in order to find the most popular types of data. Once it has the list, the crypto workflow takes effect. The structure of every such file is subject to disarrangement through cryptography, with complete inaccessibility being the ultimate objective.
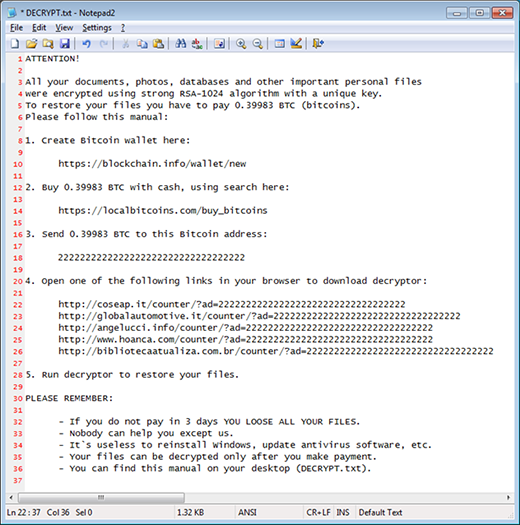
The step-by-step recovery tutorial provided by the perpetrators appears on the PC’s desktop as well as individual folders that contain one or more encoded files in them. This document is titled DECRYPT.txt. It opens up with Notepad and first conveys the following warning message, “All your documents, photos, databases and other important personal files were encrypted using strong RSA-1024 algorithm with a unique key. To restore your files you have to pay 0.39983 BTC.” In a nutshell, the victim needs to create a Bitcoin wallet, buy the right amount of cryptocurrency, send it to a particular Bitcoin address, open a page that hosts the decryptor, and run the tool to restore the data. Interestingly, the decrypt pages are regular websites rather than Tor gateways, unlike most ransomware samples at large. According to the ransom note, the user must submit the digital cash during three days otherwise the private key will supposedly be deleted from the Command and Control server.
Fortunately, there are restoration methods that do not counter the extremely strong encryption standard. Instead, they revolve around the use of data recovery software or Shadow Volume Copies, file backups made by the operating system.
Automatic removal of .crypted file virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button Download .crypted removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get .crypted automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover .crypted files ciphered by Nemucod ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: BackupsThe cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery toolsThe research of .crypted virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow CopiesThe Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
-
Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.

-
Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.

Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.



